A few weeks ago, I found an interesting ClickFix sample (e.g., a fake reCAPTCHA) during an investigation of a compromised WordPress website. A threat actor is infecting legitimate WordPress websites with a malicious Base64 Blob in the tags, which results in a fake reCAPTCHA and ClickFix trying to get the victim to run malicious codes. The user was prevented from interacting with the site until "reCAPTCHA verification" was completed. ClickFix refers to a manipulative tactic where attackers trick users into clicking on malicious elements (links, buttons, pop-ups, or fake system alerts) under the guise of fixing a problem, such as a security issue, software error, or account access problem. This type of social engineering attack exploits human psychology by creating a sense of urgency or fear, pressuring victims into taking immediate (but harmful) action. Stage 1 - Injection with...
JUMPSEC LABS
The JUMPSEC Lab is a place where the technical team get creative and showcase their latest security research, publications, interesting news and general thoughts! We love what we do and are passionate about security, with some great upcoming projects planned, bookmark our site and stick around to see what we are working on.
A Closer Look at Microsoft’s Latest Email Security Requirements – Tooling Release Included!
Email remains one of the most consistently targeted attack surfaces in cyber security. Despite evolving defences, phishing, spoofing, and impersonation attacks continue to be...
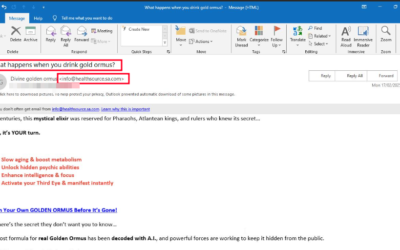
The Anatomy of a Phishing Investigation: How Attackers Exploit Health-Related Fears
JUMPSEC’s Detection and Response Team (DART) responds to many phishing threats targeting our clients. An interesting incident I recently had to respond to, was a critical alert...
Tutorial – How to setup a forward proxy with HAProxy that routes TOR through a VPN…in docker
At JUMPSEC we foster a research culture and want to provide people with tools and safe environments necessary to conduct research. As part of my ongoing work in setting up a new research lab I also wanted to investigate TOR environments. By design TOR is a privacy first process and the The Onion Router provides a very good solution out of the box. I won’t elaborate on the foundations of TOR in...
Ranking MFA Methods – From Least to Most Secure
My Perspective on MFA Security In an era of relentless cyber threats, multi-factor authentication (MFA) has become a cornerstone of modern security practices, adding an extra layer of protection beyond traditional passwords. It’s a widely used defence that strengthens account security and helps prevent unauthorised access. But while MFA is a crucial security measure, it’s not a silver bullet....
Please Mind the CAP – Modern Conditional Access Policy circumvention and what it means for your organisation (webinar recording)
Webinar recording - original session on 31 Jan 2025
Bring Your Own Trusted Binary (BYOTB) – BSides Edition
Recently, I presented a talk on the main stage at BSides London 2024 and the topic I chose to present on was in regards to bringing trusted binaries to a system and using them in an adversarial fashion. This post will cover what I presented and how to use these binaries in detail. If you would also like a copy of the slides they can be found here. My talk was mainly focused on binaries that...
TokenSmith – Bypassing Intune Compliant Device Conditional Access
Conditional Access Policies (CAPs) are the core of Entra ID’s perimeter defense for the vast majority of Enterprise Microsoft 365 (M365) and Azure environments. The core ideas of conditional access are: Require specific auth strength in scenarios where you wish to grant access Block access in undesirable scenarios If a scenario are neither covered by a or b, then the minimal auth strength...
BCP, as easy as ABC?
A Business Continuity Plan (BCP) is a strategic playbook created to help an organisation maintain or quickly resume business functions in the face of disruption. (Pratt, Tittel, Lindros, 2023) Be honest now. Who really has a truly effective Business Continuity Plan in 2024? Not the compliance-driven plan that has not been reviewed or tested properly for years. Or the “oh no, this supplier...
Weaponize Your Word – Malicious Template Injection
Weaponize Your Word - Malicious Template Injection Historically, files sent via email have been a common initial access technique employed by threat actors. Personally, I have seen emails containing malware prove effective, and in the case of an IR (Incident Response) involving a malware infection, it would be one of the first places I would look to identify the source of compromise. There are...
Breaking into Libraries – DLL Hijacking
Breaking into Libraries - DLL Hijacking Many of us have likely encountered DLL errors when trying to open Windows applications. If you were like my younger self, you might have naively downloaded a missing DLL from sites like dll-files.com and placed it in the application directory without giving it a second thought. This blog post will examine the risks associated with this approach. Dynamic...
Disclaimer
The information provided on this website is to be used for educational purposes only. The author is in no way responsible for any misuse of the information provided. Any actions and or activities related to the material contained within this website is solely your responsibility.