JUMPSEC’s Detection and Response Team (DART) responds to many phishing threats targeting our clients. An interesting incident I recently had to respond to, was a critical alert titled “multi-stage alert involving Initial Access & Lateral Movement”.
This alert was triggered by a series of phishing emails targeting individuals with lures presenting a common theme. In this LABS post, I’ll walk you through the investigation, how we pieced together several bits of information to figure out the tactics and infrastructure used by the attackers, and the steps taken to mitigate the threat.
Incident Overview
Microsoft Defender XDR (eXtended Detection and Response) triggered the alert that four emails matched our alert policy relating to “malicious URL that were delivered and later removed”.
Using the “Email Preview” feature in Defender, I was able to see that all the phishing emails shared a common theme: health products. These emails were designed to trick victims potentially concerned about their health, into clicking malicious links.
Email Lures
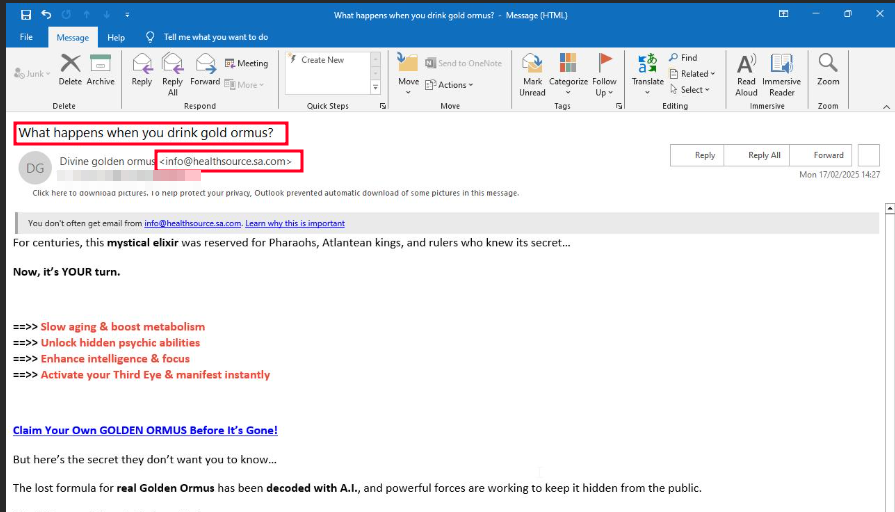
Figure 1. Email from Healthsource
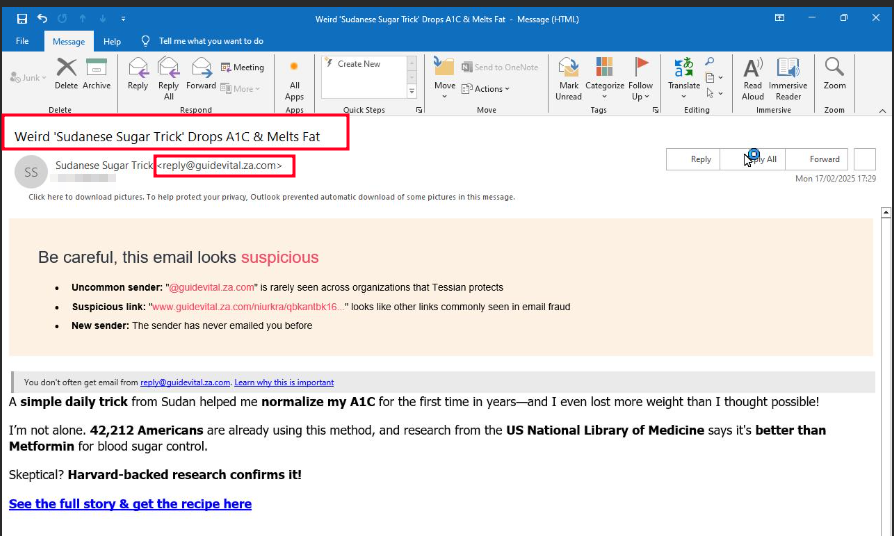
Figure 2. Email from GuideVital
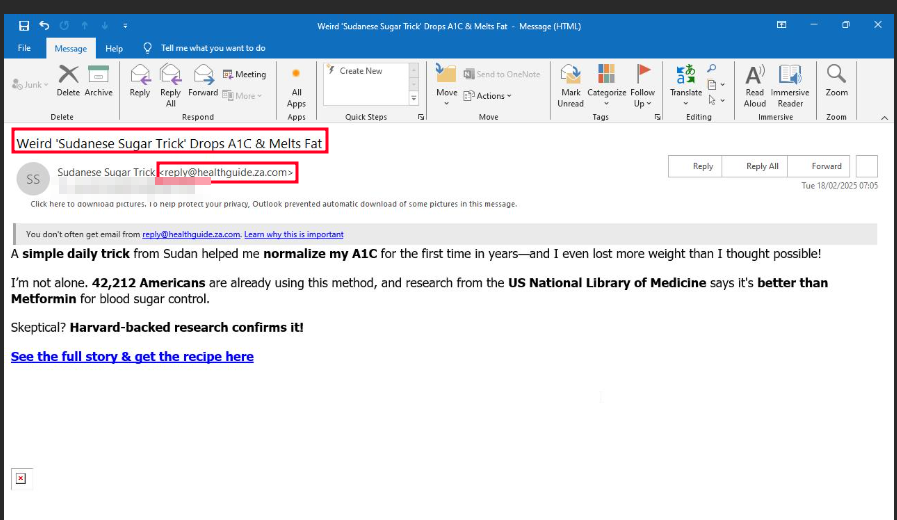
Figure 3. Email from HealthGuide
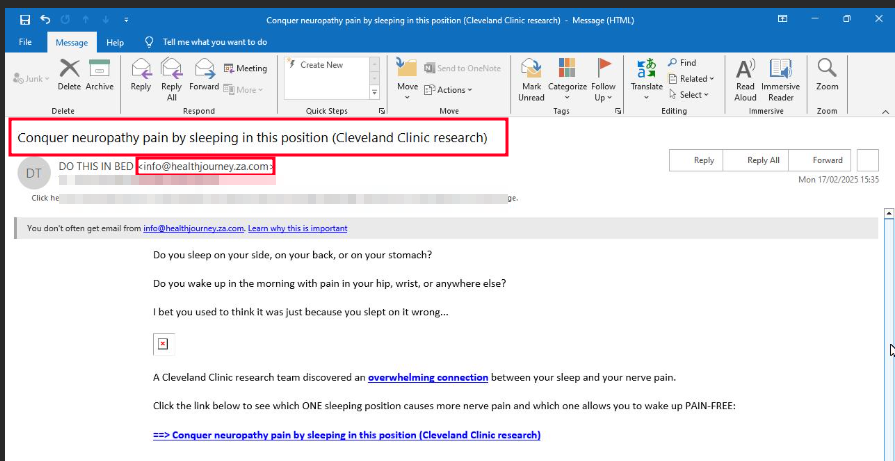
Figure 4. Email from HealthJourney
The Attack Chain
The phishing campaign followed a multi-stage process designed to deceive victims and extract sensitive information (e.g. bank details, account credentials, etc.). The first step involved sending users health-related emails, which contained malicious links. When a victim clicks the malicious link, they are redirected to a page displaying a “Human Verification Check.”
Such web page was hosted on a domain that matched the sender’s domain, such as reply[@]guidevital[.]za[.]com, adding a layer of legitimacy to the scam.
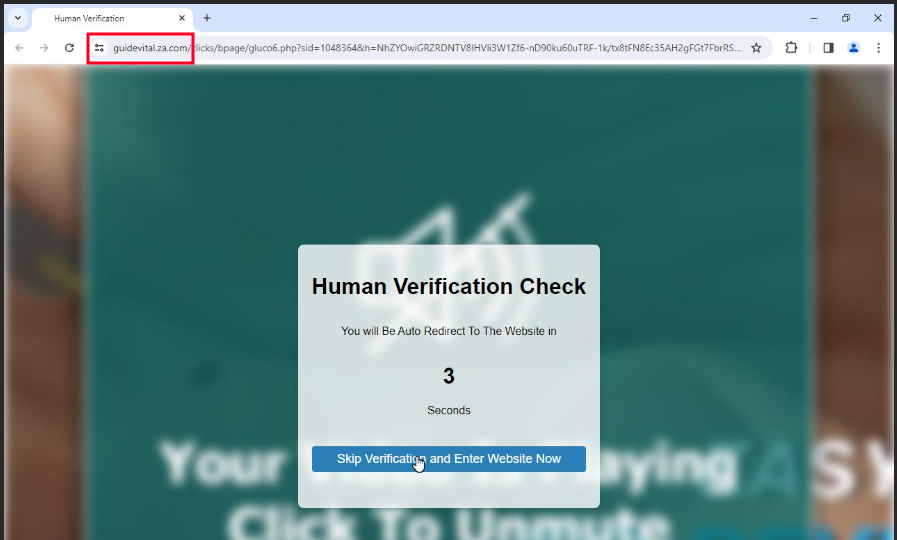
Figure 5. Human Verification page from GuideVital
After completing the verification step, victims were redirected to a shopping website presenting the domain gluco6[.]com, which was used for phishing. The website was designed to mimic a legitimate online store, complete with product listings and shopping cart functionality.
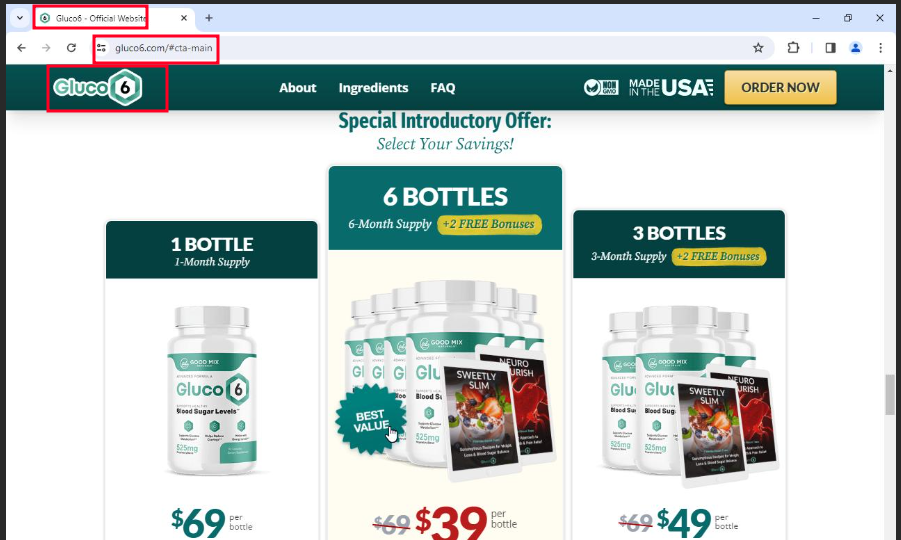
Figure 6. Phishing Shopping Website with Gluco6
Clicking the “ADD TO CART” button redirected users to a payment page hosted on clickbank[.]net, a legitimate online marketplace often leveraged by scammers. This final step was intended to trick victims into entering their payment details, making them believe that they were making a legitimate purchase.

Figure 7. Payment page with PayPal from ClickBank
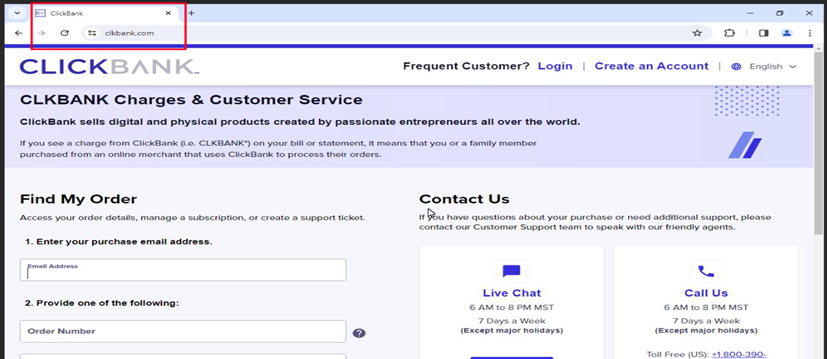
Figure 8. ClickBank Website
Additional Phishing Emails
Another set of emails from info[@]healthsource[.]sa[.]com followed a similar pattern to the one above, redirecting users to a shopping website with the domain enkielixir[.]com.
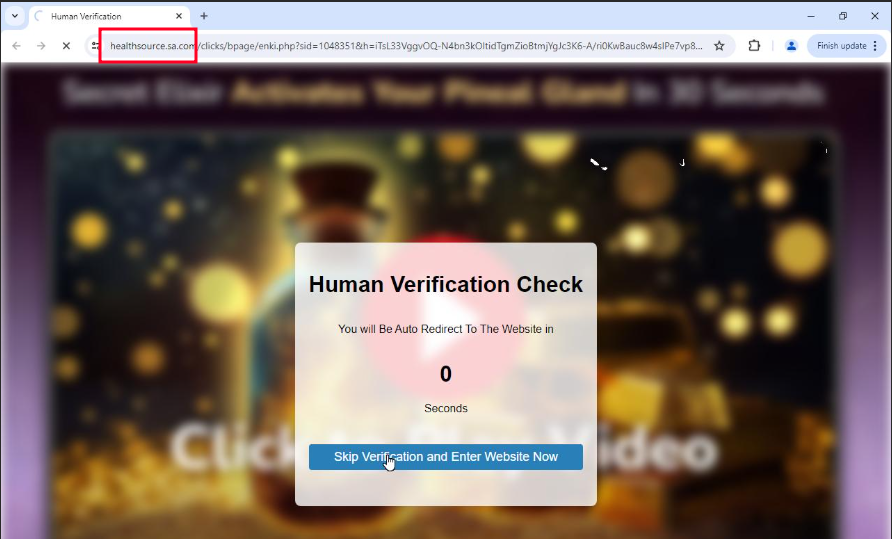
Figure 9. Human Verification page from HealthSource
During the investigation, I identified 10 additional emails originating from the same phishing domains. These emails were promptly flagged by Microsoft Defender as High likelihood of Phishing and were quarantined. This action ensured that recipients could not access the malicious links or phishing websites while investigating. To further mitigate the threat, I then blocked all associated malicious domains, including the sender domains and the scam shopping websites.
This proactive measure helped prevent further exposure to the phishing campaign and disrupted the scammer’s operations.
Threat Hunting
Following the investigation, it was critical to ensure that no threat actors managed to compromise sensitive data and an in-depth hunt was in order. In this section, we are going to delve into the investigative steps taken to uncover the infrastructure behind the phishing campaign.
By analysing shared host keys, IP addresses, and network behaviours, we were able to identify connections between multiple sender domains and confirm that they were operated by the same threat actor. This section also outlines the actions taken to block malicious IPs and domains, preventing further phishing attempts.
Unlike reactive security measures that wait for alerts to trigger, high-quality threat hunting is proactive, seeking to identify threats before they cause significant damage.
Uncovering the attacker’s Infrastructure
Our investigation began with the assumption that all the sender domains were owned by the same scammer, as they shared same email themes.
To validate this, we started by checking the IP address of one of the sender domains, healthsource[.]sa[.]com. We discovered that it was hosted on 23[.]94[.]153[.]80
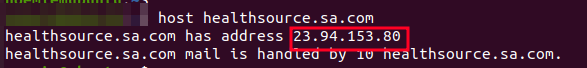
Figure 10. IP of Healthsource Domain
Further investigation revealed a shared host key (9eb62e29c1e17d77f010a65efe2cb2b21782e38da013af2dfc2ff36f8f508a6f) across 25 hosts. This finding was significant because it suggested that such hosts were likely controlled by the same individual or organization.
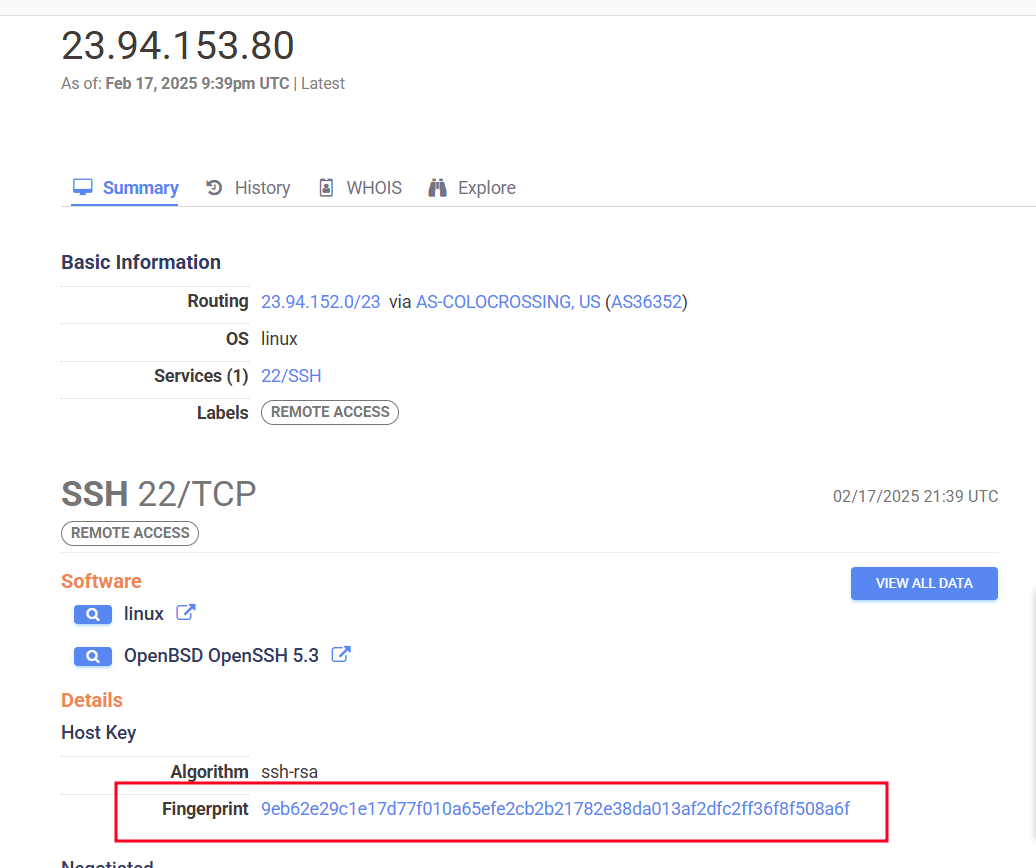
Figure 11. Host Key Information from Censys
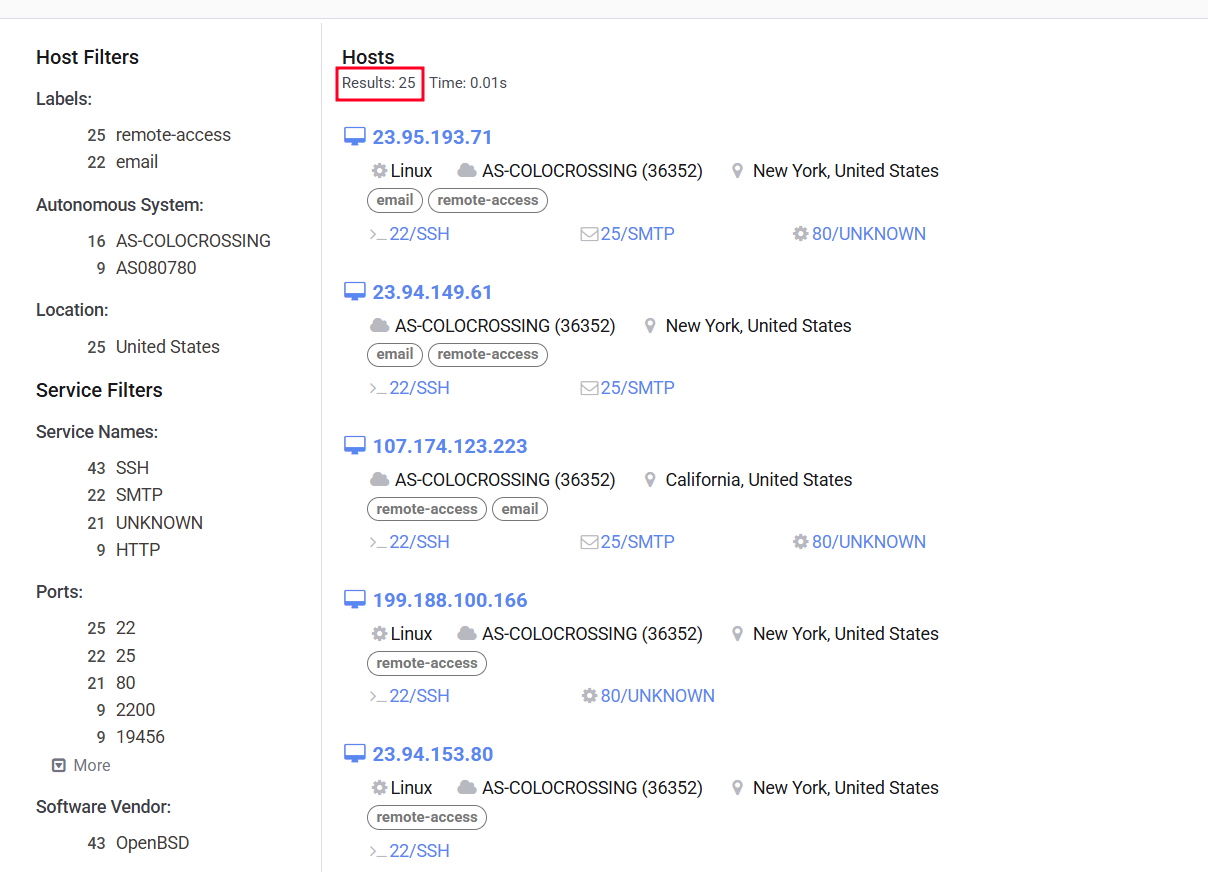
Figure 12. List of 25 Hosts sharing the same key
Among these 25 hosts, we found the three sender domains identified by the alert, confirming our initial assumption. This discovery allowed us to connect the dots and understand the broader infrastructure used by the malicious actor.
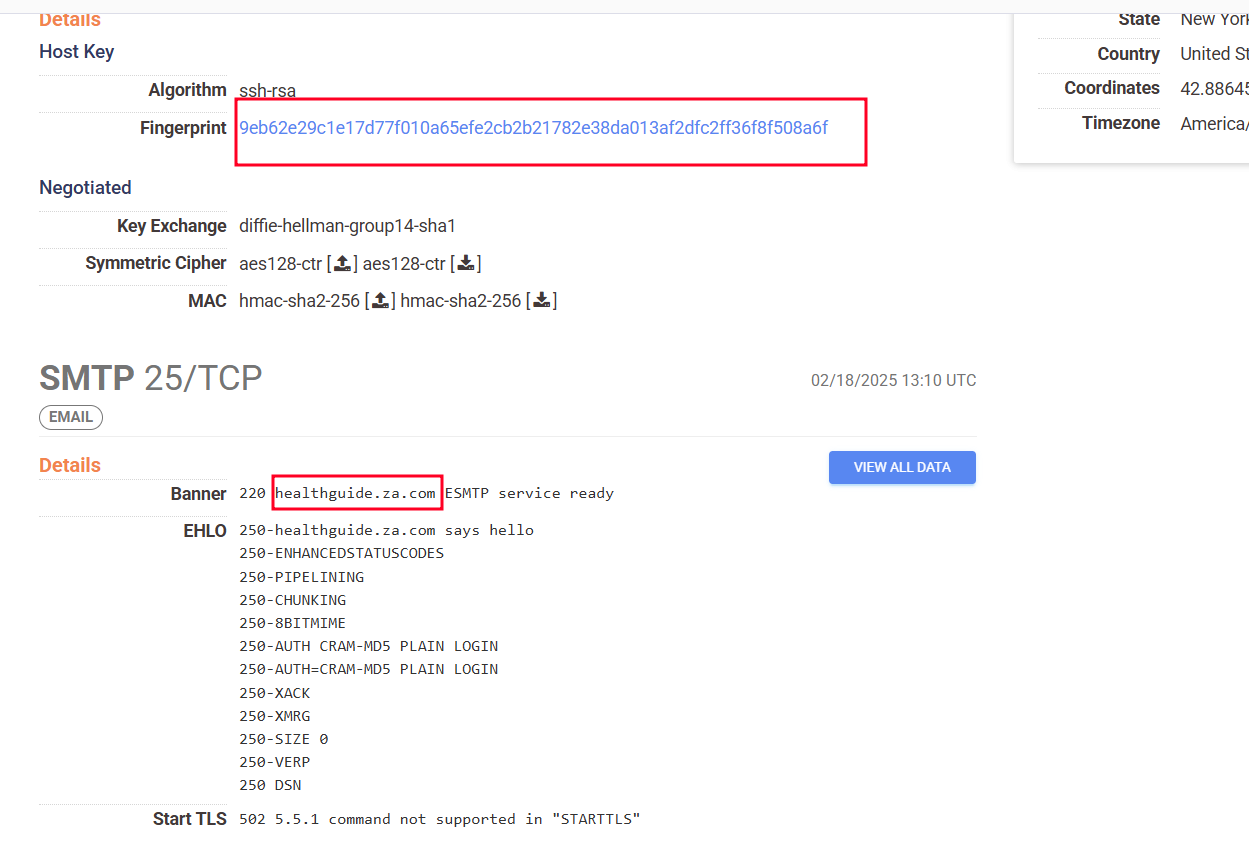
Figure 13. Sender domain HealthGuide info
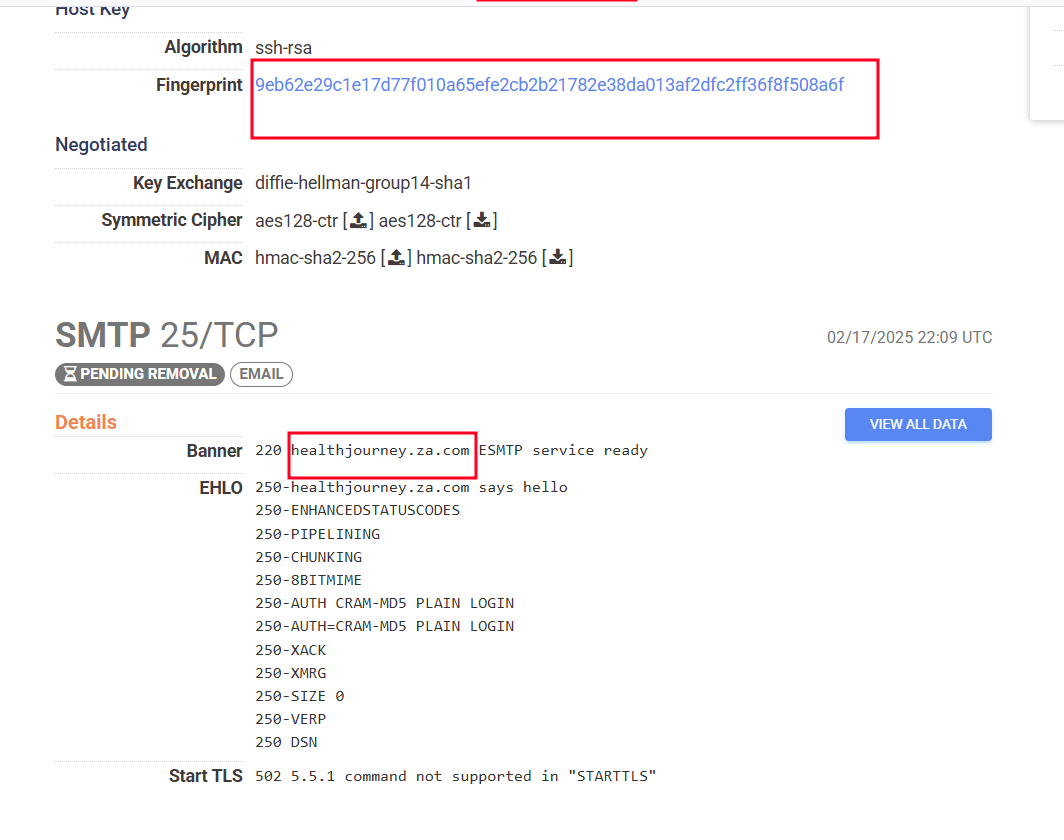
Figure 14. Sender domain HealthJourney Info
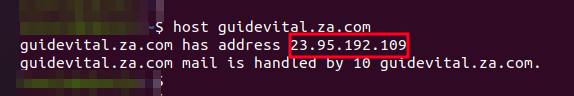
Figure 15. Sender domain GuideVital Info
To mitigate the threat, we blocked all 25 malicious IP addresses associated with these hosts. This action prevented further phishing attempts from these IPs and likely disrupted the scammer’s operations.
IPs for Phishing Shopping Websites
Next, the focus shifted to the IP addresses associated with the phishing shopping websites. The IPs for website gluco6[.]com were part of CLOUDFLARENET (104.20.0.0/15,172.67.0.0/16). While Cloudflare itself is not designed for phishing, malicious actors can sometimes use Cloudflare’s services to mask their phishing attempts by leveraging its features like content delivery networks (CDNs) to make their phishing websites appear more legitimate, thus making it harder to detect and block them.
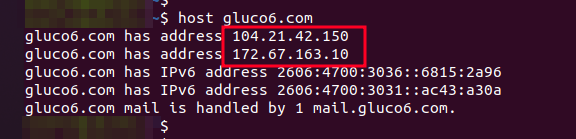
Figure 16. IPs info fo gluco6 domain.
![Figure 17. 104[.]21[.]42[.]150 info from VirusTotal Figure 17. 104[.]21[.]42[.]150 info from VirusTotal](https://labs.jumpsec.com/wp-content/uploads/sites/2/2025/03/Figure-18.-104.21.42.150-info-from-VirusTotal.png)
Figure 17. 104[.]21[.]42[.]150 info from VirusTotal
![Figure 18. 172[.]67[.]163[.]10 info from VT Figure 18. 172[.]67[.]163[.]10 info from VT](https://labs.jumpsec.com/wp-content/uploads/sites/2/2025/03/Figure-19.-172.67.163.10-info-from-VT.png)
Figure 18. 172[.]67[.]163[.]10 info from VT
Similarly, the IP of enkielixir[.]com is from LIQUID WEB (AS-32244).
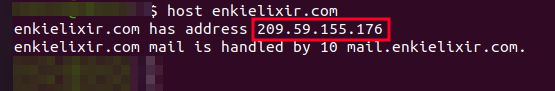
Figure 19. IP info of enkielixir domain
![Figure 20. 209[.]59[.]155[.]176 info from Virustotal Figure 20. 209[.]59[.]155[.]176 info from Virustotal](https://labs.jumpsec.com/wp-content/uploads/sites/2/2025/03/Figure-21.-209.59.155.176-info-from-Virustotal.png)
Figure 20. 209[.]59[.]155[.]176 info from Virustotal
Again, we blocked 3 IPs of the phishing shopping websites.
Second Alert: A Repeat Offender
Another alert was triggered by four similar emails in Microsoft Defender. The emails directed users to a new phishing shopping website: metanailcomplex[.]com.
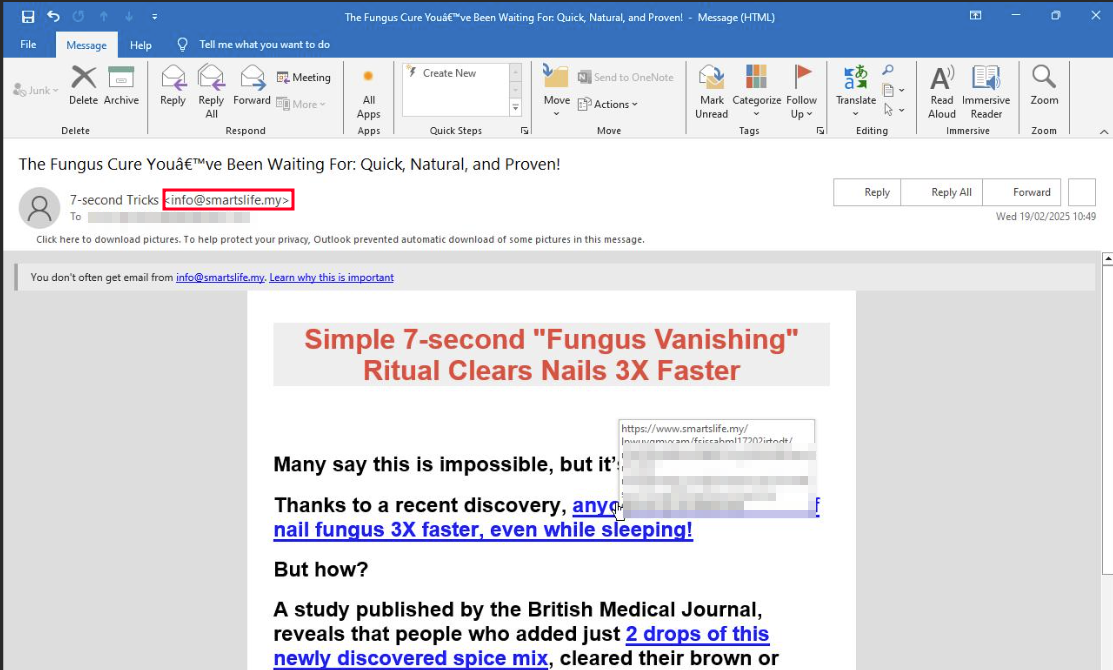
Figure 21. Email from SmartsLife
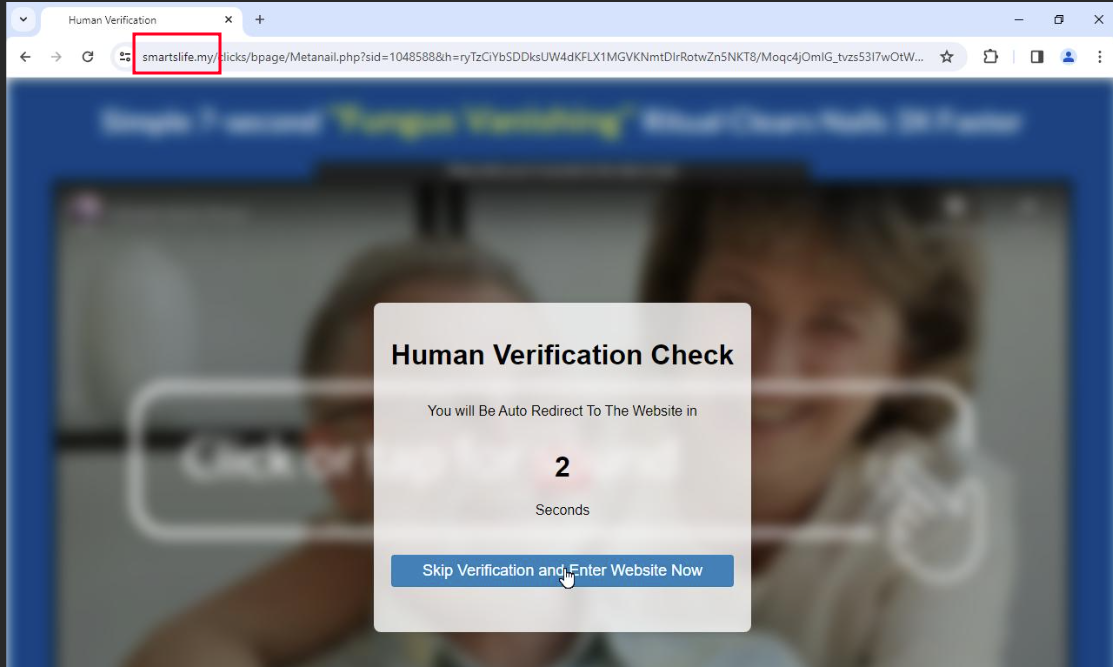
Figure 22. Human Verification page from SmartsLife
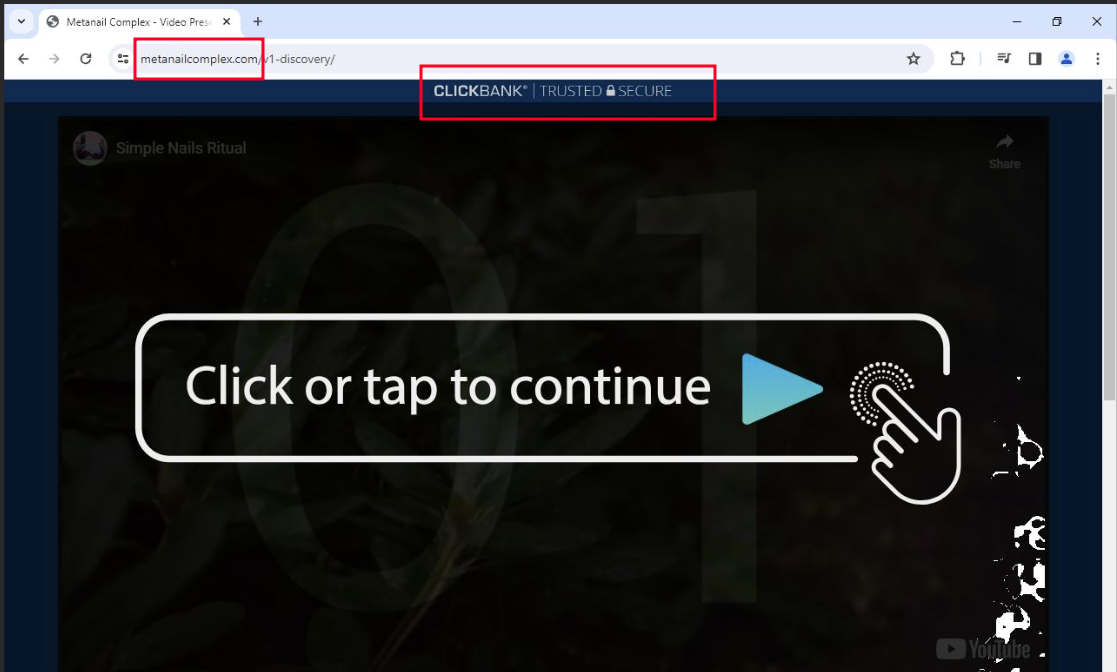
Figure 23. Phishing shopping website metanailcomplex
The IPs for this shopping website were part of CLOUDFLARENET(104.20.0.0/15) same as the IP of domain gluco6[.]com. Many IP addresses from this were labeled as malicious, further confirming the scammer’s reliance on this network.
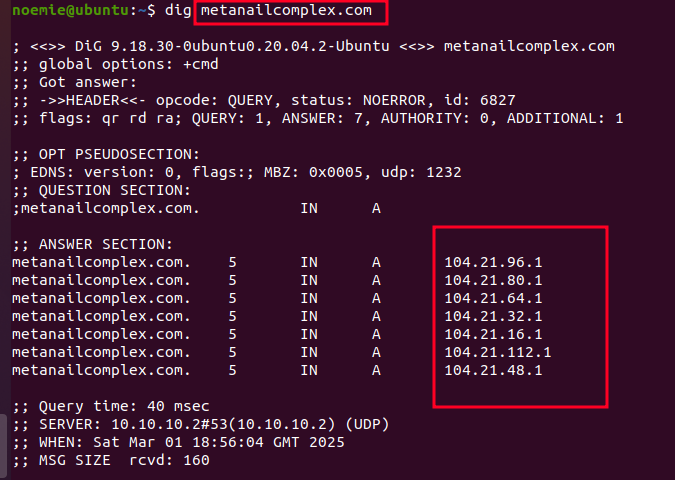
Figure 24. IP info of domain metanailcomplex
![Figure 25. IP 104[.]21[.]96[.]1 info from Virustotal Figure 25. IP 104[.]21[.]96[.]1 info from Virustotal](https://labs.jumpsec.com/wp-content/uploads/sites/2/2025/03/Figure-26.-IP-104.21.96.1-info-from-Virustotal.png)
Figure 25. IP 104[.]21[.]96[.]1 info from Virustotal
![Figure 26. Malicious IPs in ip range 104[.]20[.]0[.]0/15 Figure 26. Malicious IPs in ip range 104[.]20[.]0[.]0/15](https://labs.jumpsec.com/wp-content/uploads/sites/2/2025/03/Figure-27.-Malicious-IPs-in-ip-range-104.20.0.015.png)
Figure 26. Malicious IPs in ip range 104[.]20[.]0[.]0/15
Connecting the Dots
The sender domain’s IP (199[.]188[.]100[.]170) was in the same subnet as the IP we found shared same host key(199[.]188[.]100[.]166).
This connection reinforced the belief that the same threat actor was behind both campaigns.
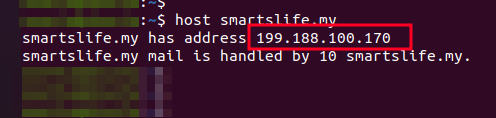
Figure 27. IP info of SmartsLife domain
![Figure 28. 199[.]188[.]100[.]170 info from VT Figure 28. 199[.]188[.]100[.]170 info from VT](https://labs.jumpsec.com/wp-content/uploads/sites/2/2025/03/Figure-29.-199.188.100.170-info-from-VT.png)
Figure 28. 199[.]188[.]100[.]170 info from VT
![Figure 29. 199[.]188[.]100[.]166 info from VT Figure 29. 199[.]188[.]100[.]166 info from VT](https://labs.jumpsec.com/wp-content/uploads/sites/2/2025/03/Figure-30.-199.188.100.166-info-from-VT.png)
Figure 29. 199[.]188[.]100[.]166 info from VT
Further analysis revealed that most of the 25 scammer IPs belonged to AS-36352, a network with a poor reputation.
An ASN, or Autonomous System Number, is a unique identifier assigned to a group of IP networks (an autonomous system) that share a common routing policy, enabling efficient routing of data across the internet.
This network was associated with multiple malicious activities, making it a key focus of our investigation.
(source: https://www.ip2location.com/as36352, https://www.ipqualityscore.com/asn-details/AS36352/colocrossing, https://www.virustotal.com/gui/search/entity%253Aip%2520as_owner%253AAS-COLOCROSSING?type=ips)
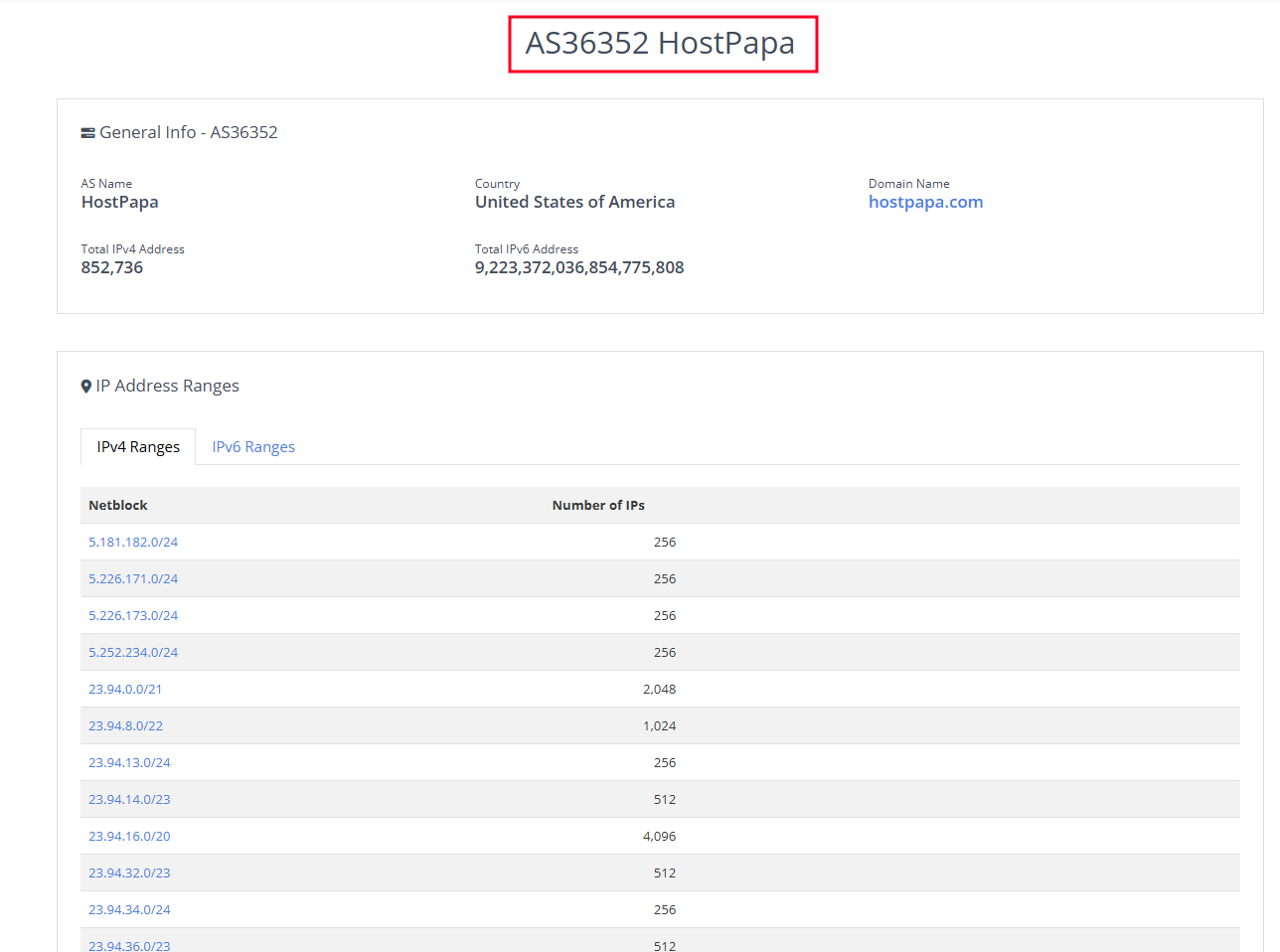
Figure 30. AS-36352 Network Information
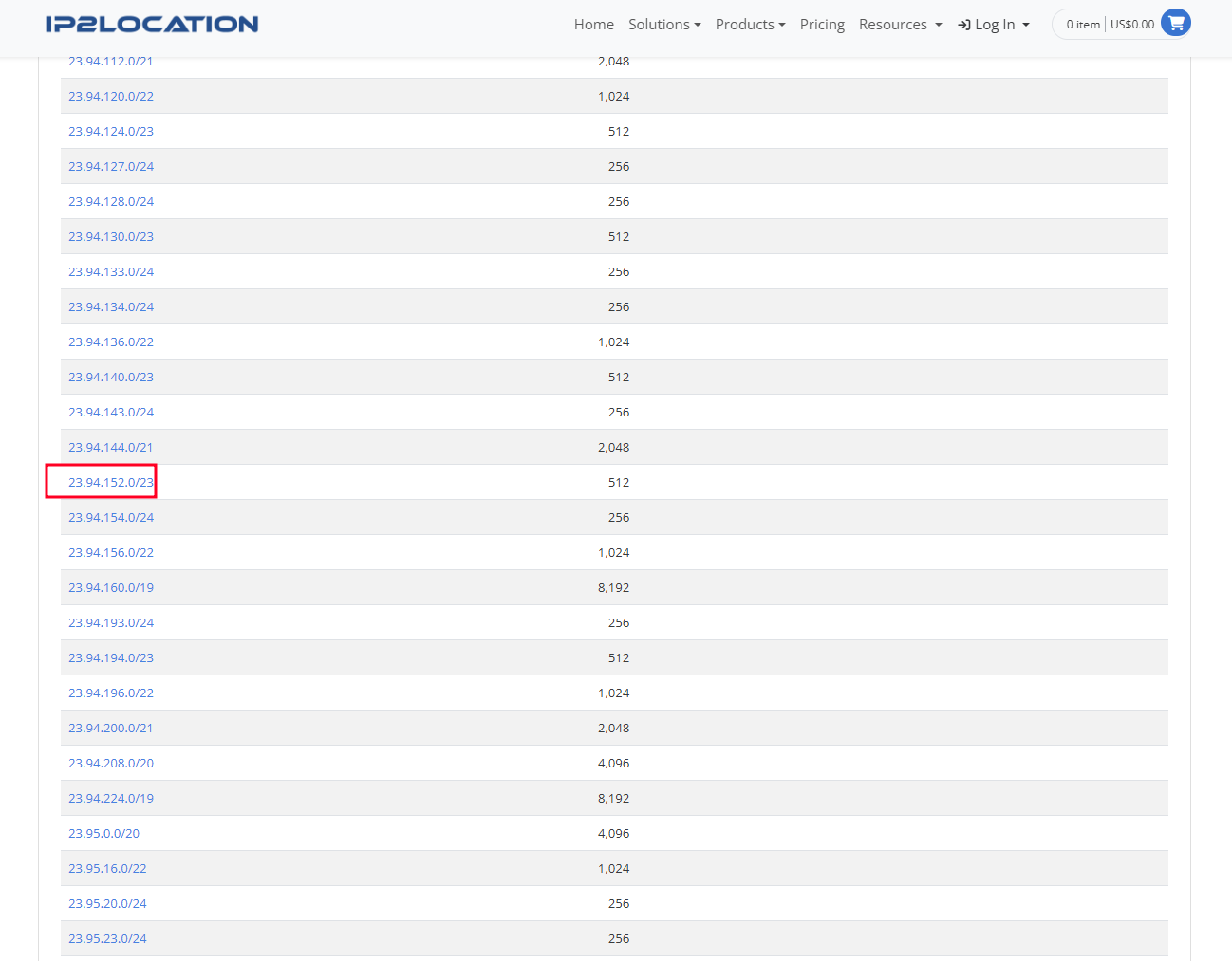
Figure 31. IP range of the IP we found early
Then discovering that the ISP for these IPs had a history of malicious activity.
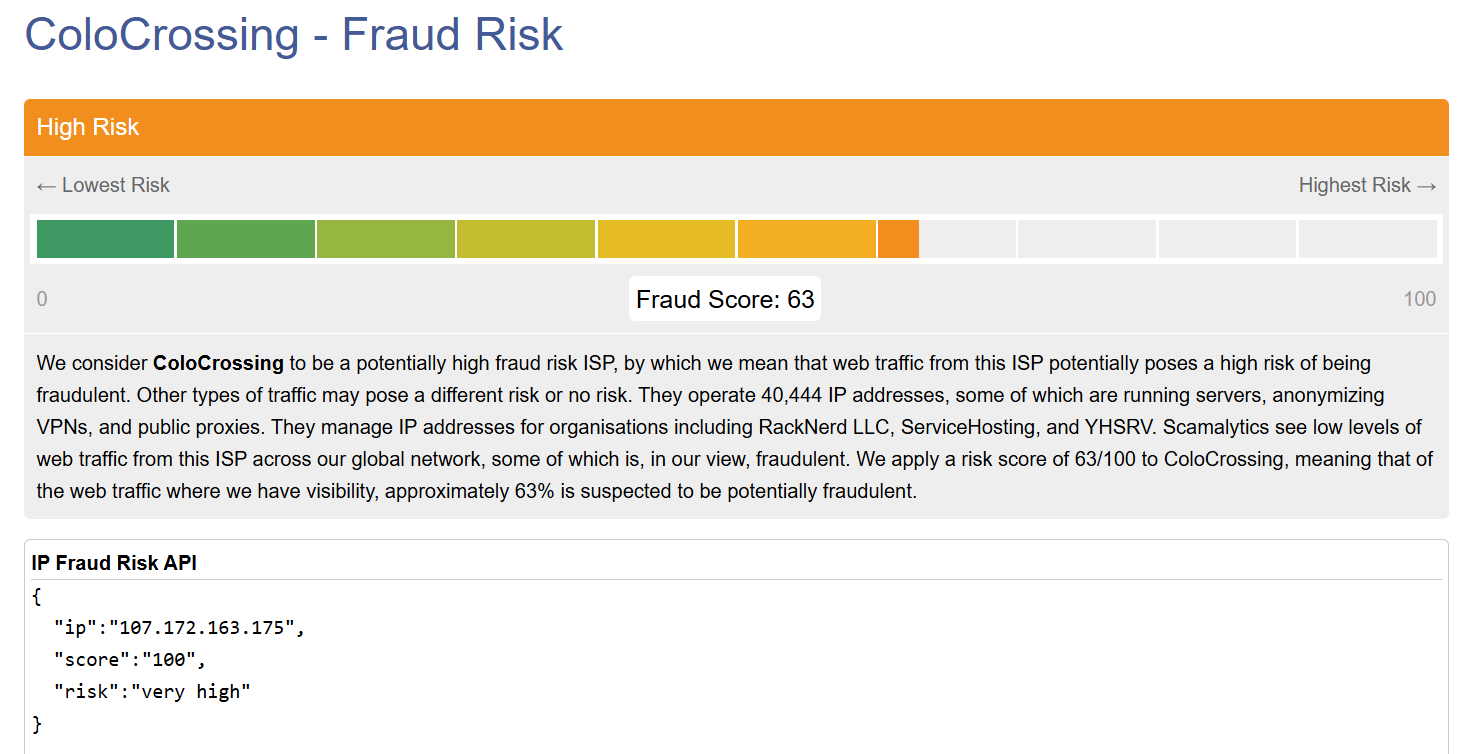
Figure 32. ISP Reputation Analysis
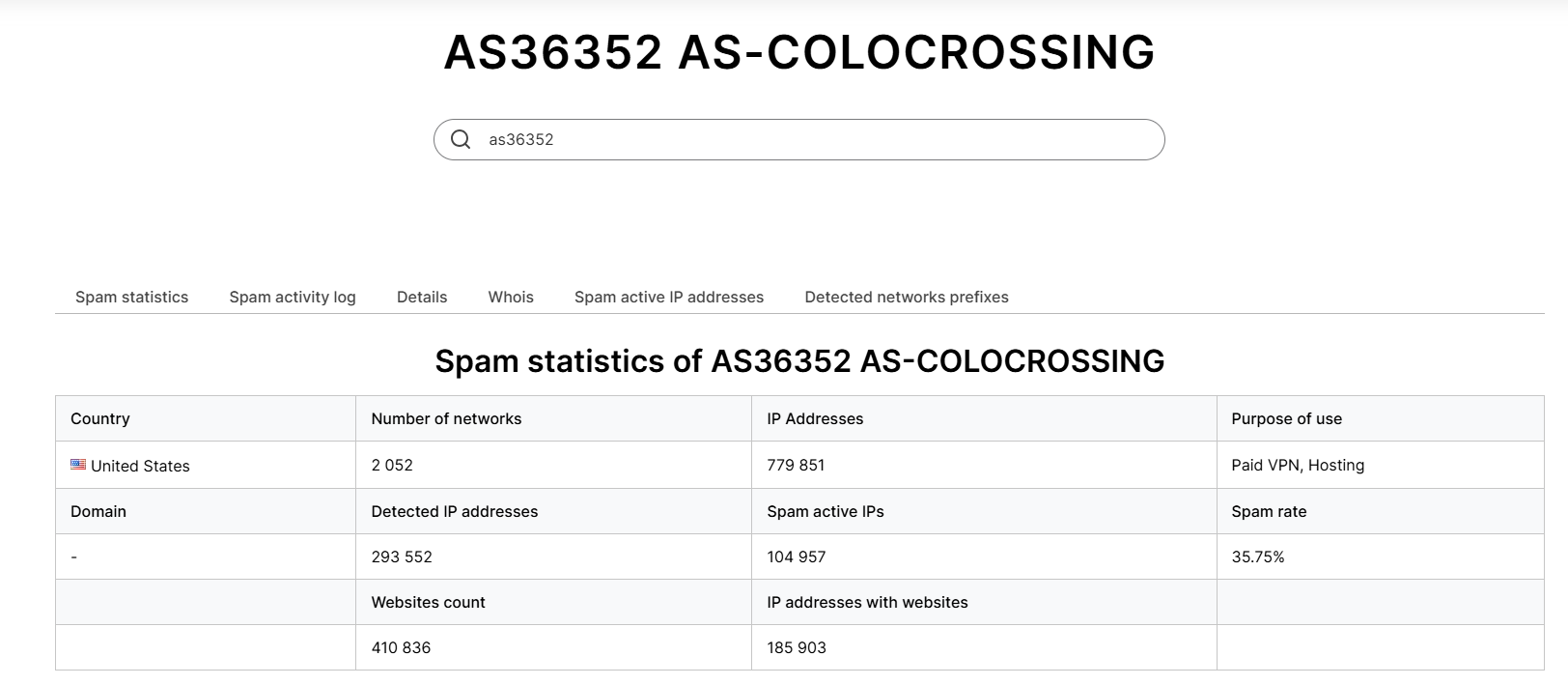
Figure 33. ISP Malicious Activity Report
The final piece investigated was related to the IP 74.114.x.x that did not belong to the risky ASN (AS-36352), showing the ISP as Clnetworks Inc on the AS-32987 ASN.
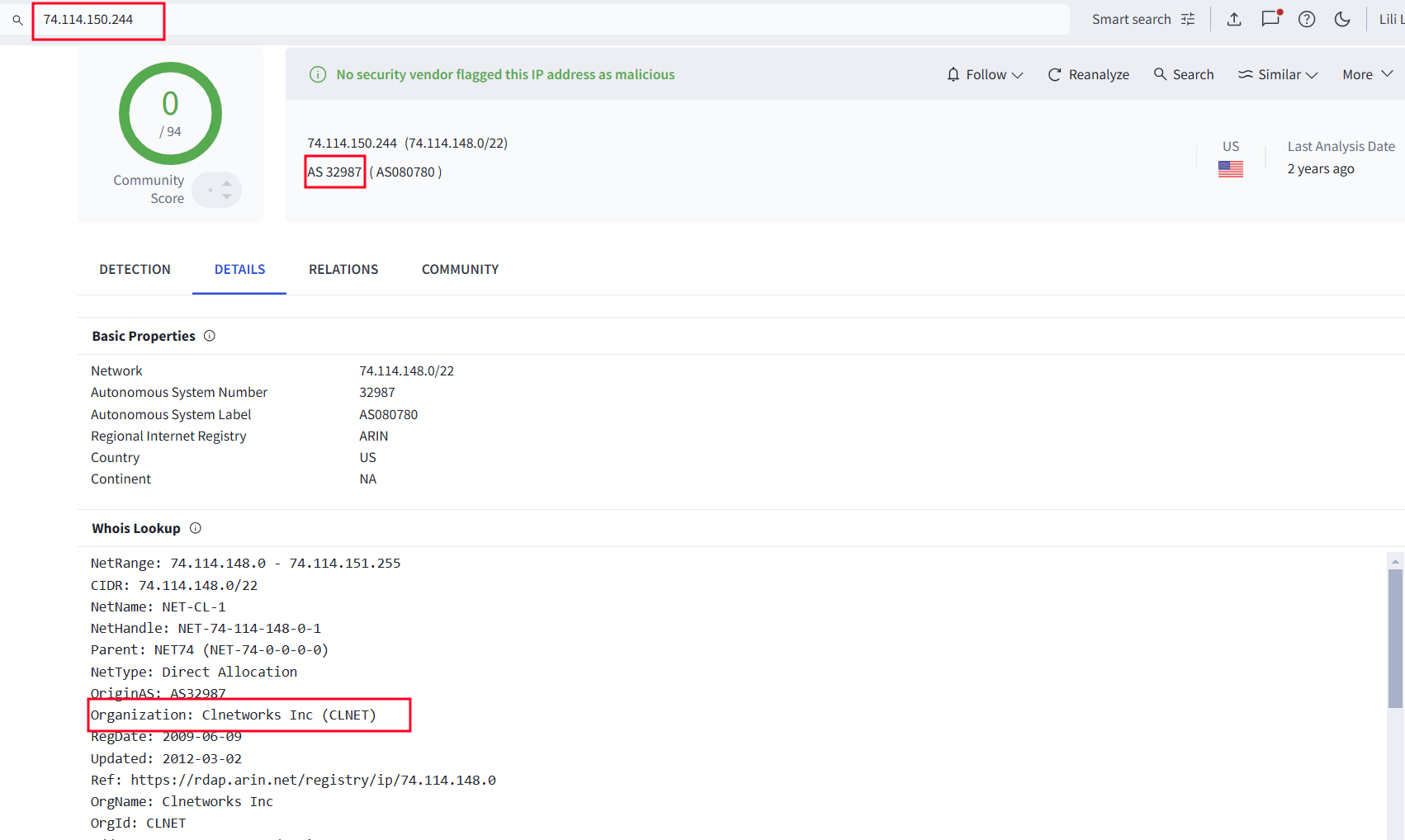
Figure 34. IP Details for 74.114.x.x
Conclusions
This investigation uncovered a intricate phishing campaign that blended health-related lures with legitimate services like ClickBank and Cloudflare to evade detection. By analysing shared host keys, we uncovered the connections between multiple sender domains, and can confirm that they were operated by the same threat actor, highlighting the importance of threat hunting in identifying hidden infrastructure and prevent future attacks.
Using CLOUDFLARENET for hosting phishing websites shows how hackers are widely using legitimate platforms to carry out attacks. There is plenty of space for such legitimate networks provider to check the legitimacy of the registers (individuals, organisation).
Considering most users cannot recognize malicious emails, websites, documents and phishing events, companies should take a proactive stance on training users on security awareness as well as enhancing email security to tackle phishing campaigns’ commonly used tactics.
Recommendations
To mitigate similar phishing campaigns in the future, organizations should adopt a multi-layered approach that combines technical defenses with user education. Below are some key recommendations – particularly relevant for organisations leveraging the Microsoft Defender stack – to strengthen defences against evolving phishing threats:
- Create Watchlists: Hunting any suspicious emails from IPs that are from AS-36352, AS-32987, and AS-32244s. Monitor for the mentioned malicious CLOUDFARENET IP addresses.
- Enhance Email Security: Organisations using Defender can take advantage of its detection capabilities for most phishing emails, flagging and showing them as a highly likely phishing attempt. Implementing additional advanced phishing detection tools to quarantine suspicious emails automatically can include custom detections, or other proprietary solutions.
- User Awareness: Last but not least, it is important to educate employees about phishing tactics, especially those involving health-related or other common lures associated to basic necessities exploiting the human factor.
Indicator Of Compromise Identified:
Scammer Email IPs:
23[.]95[.]192[.]109
23[.]94[.]153[.]80
23[.]95[.]193[.]70
23[.]95[.]193[.]67
23[.]94[.]149[.]61
23[.]95[.]193[.]69
23[.]94[.]153[.]79
23[.]95[.]193[.]68
199[.]188[.]100[.]166
23[.]95[.]192[.]110
107[.]174[.]123[.]220
107[.]174[.]123[.]223
23[.]95[.]193[.]71
74[.]114[.]150[.]248
74[.]114[.]150[.]244
74[.]114[.]150[.]247
107[.]174[.]123[.]224
74[.]114[.]150[.]251
74[.]114[.]150[.]246
74[.]114[.]150[.]253
74[.]114[.]150[.]254
74[.]114[.]150[.]243
74[.]114[.]150[.]252
23[.]95[.]192[.]111
199[.]188[.]100[.]170
IP addresses of malicious shopping websites:
104[.]21[.]42[.]150
172[.]67[.]163[.]10
209[.]59[.]155[.]176
