Software: IBM SAN Volume Controller, IBM Storwize, IBM FlashSystem and IBM Storage Virtualize products Affected versions: 8.3 Vendor page: https://www.ibm.com/support/pages/node/7064976 CVE Reference: CVE-2023-43042 Published: 08/12/2023 CVSS 3.0 Score: 7.5 AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N Attack Vector: Network Credit: Max Corbridge Summary JUMPSEC’s Head of Adversarial Simulation (@CorbridgeMax) discovered that an unauthenticated user can determine whether the default superuser password has been changed on IBM SAN Volume Controller, IBM Storwize, IBM FlashSystem and IBM Storage Virtualize products. These products were found to be a single point of failure for backup and disaster recovery processes within client environments, and as such are highly critical systems. This only affects the 8.3.1 release as it is impossible for the default password to still be configured on an active...
JUMPSEC LABS
The JUMPSEC Lab is a place where the the technical team get creative and showcase their latest security research, publications, interesting news and general thoughts! We love what we do and are passionate about security, with some great upcoming projects planned, bookmark our site and stick around to see what we are working on.
Red Teaming the Cloud: A Shift in Perspective
Having delivered entirely cloud red teams, JUMPSEC experts discuss the shifts in perspective necessary for red teamers when targeting cloud environments.
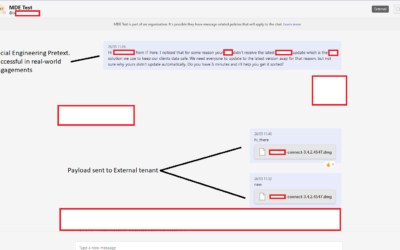
Advisory: IDOR in Microsoft Teams Allows for External Tenants to Introduce Malware
TL;DR Max Corbridge (@CorbridgeMax) and Tom Ellson (@tde_sec) of JUMPSEC’s Red Team recently discovered a vulnerability in the latest version of Microsoft Teams which allows for...
Hunting the Snake: An Overview of Threat Hunting with Velociraptor
In May 2023 the NCSC and CISA released a joint cyber security advisory addressing a piece of Russian malware called Snake. According to them, this malware has been gathering intelligence for the FSB in more than 50 countries for the last 20 years. Off the back of this advisory JUMPSEC decided to perform a number of threat hunts to provide assurance for some of our clients. Whilst conducting...
Ligolo: Quality of Life on Red Team Engagements
In recent months we, JUMPSEC’s red team, have been using a nifty little tool that we would like to share with you in this blog post. Ligolo-ng is a versatile tool that has been aiding our covert, and slightly-less-covert, engagements with regards to tunnelling, exfiltration, persistence, and widely improving the operators’ “quality of life” when carrying out assessments involving beaconing from...
Hunting for ‘Snake’
Following the NCSC and CISA’s detailed joint advisory on the highly sophisticated ‘Snake’ cyber espionage tool, JUMPSEC threat intelligence analysts have provided a condensed blueprint for organisations to start proactively hunting for Snake within their network, contextualising key Indicators of Compromise (IoC), and providing additional methods to validate the effectiveness of Snake...
Advisory CVE-2023-30382 – Half-Life Local Privilege Escalation
Software: Half-Life Affected versions: Latest (<= build 5433873), at the time of writing Vendor page: www.valvesoftware.com CVE Reference: CVE-2023-30382 Published: 23/05/2023 CVSS 3.1 Score: 8.2 AV:L/AC:L/PR:L/UI:R/S:C/C:H/I:H/A:H Attack Vector: Local Credit: Ryan Saridar Summary An attacker can leverage a stack-based buffer overflow via Half-Life’s command line arguments to compromise the...
Butting Heads with a Threat Actor on an Engagement
After compromising a sensitive external server JUMPSEC’s Red Team found that they were not the first ones there…
Advisory CVE-2022-37832 – Mutiny Network Monitoring Appliance hardcoded credentials
Software: Mutiny Network Monitoring Appliance Affected versions: <= 7.2.0-10855 Vendor page: www.mutiny.com CVE Reference: CVE-2022-37832 Published: 16/12/2022 CVSS 3.1 Score: 10.0 AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H Attack Vector: Network Credit: Ryan Saridar Summary An attacker can log in as root remotely to the appliance via SSH. Mitigation Upgrade to version 7.2.0-10855 onwards to...
Online Machine Learning: how to integrate user feedback
When designing and implementing a machine learning model, ensuring it is continually updated is a challenge that all engineers encounter. In this article, I explore the online machine learning technique that I used during a project and present how it was implemented for effective results. Choosing a machine learning method Machine learning solutions can be mainly split into offline and...
Implementation and Dynamic Generation for Tasks in Apache Airflow
I recently worked on a project focused on log anomaly detection using manageable machine learning pipelines. The pipelines mainly include data collection --- feature extraction --- feature engineering --- detection/prediction --- updating (maintenance). It’s important to have a solid UI to manage the pipelines so I can easily review the chain of pipelines. After much research, I found many...
Disclaimer
The information provided on this website is to be used for educational purposes only. The author is in no way responsible for any misuse of the information provided. Any actions and or activities related to the material contained within this website is solely your responsibility.