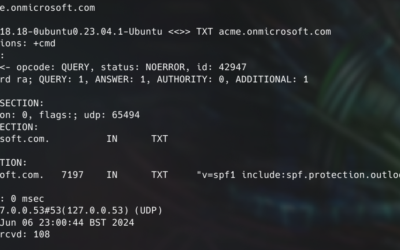
Weaponize Your Word - Malicious Template Injection Historically, files sent via email have been a common initial access technique employed by threat actors. Personally, I have seen emails containing malware prove effective, and in the case of an IR (Incident Response) involving a malware infection, it would be one of the first places I would look to identify the source of compromise. There are many techniques for bypassing an email solution to deploy malware on an endpoint, however an old technique that is worth taking note of is that of malicious template injection. This technique allows for a document that is almost entirely non-malicious to be received by a user before an actual malicious loader is pulled via the Microsoft Word remote template functionality. This technique was observed being used by the LockBit Ransomware Gang (1) early in the year. Malicious templates and...
JUMPSEC LABS
The JUMPSEC Lab is a place where the technical team get creative and showcase their latest security research, publications, interesting news and general thoughts! We love what we do and are passionate about security, with some great upcoming projects planned, bookmark our site and stick around to see what we are working on.
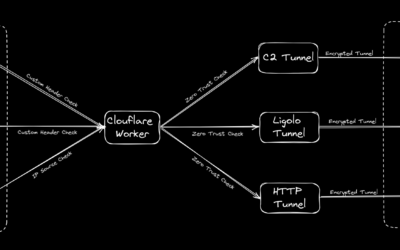
Putting the C2 in C2loudflare
tl;dr How to bring up an entire C2 infrastructure with all your tooling and their corresponding redirectors within 5 minutes with the help of Azure Snapshots, Cloudflare and Tmux...
Bullet Proofing Your Email Gateway
In this labs post, I will introduce you to modern security controls that are currently used (but not always correctly) by the vast majority of enterprises, and hopefully by the...
Microsoft Onenote Image Caching Bug (Confidential Information Leakage)
Bug Summary A security bug in the Microsoft Onenote allows images placed in user-created password-protected sections to be cached persistently in the user profile temporary directory folder: C:\Users\%username%\AppData\Local\Temp. Analysing the content the temporary folder will reveal images that should be securely protected by Onenote. Bug Scope This has only been tested with Microsoft...
Ghost In The Shellcode 2015 CTF: Write-up for cloudfs challenge
Hello there, in this post I will describe how I solved the cloudfs challenge of Ghost In The Shellcode 2015. This challenge was under the Forensics category and was awarded 200 points (middle ground!). It wasn't so hard, and someone could argue that shouldn't award the same points with "the alpha molecular" or the similars from the crypto category but it's okay (it's very common actually in...
LAYER 8 – Patching the un-patchable….
Computer systems and software have been continually evolving year upon year. Faster processing and data transfer coupled with more accessible storage have made crunching vast amounts of data possible in mere nanoseconds. Computer security and controls have improved as well, we now have intelligent firewalls, web proxies, file integrity monitoring, DLP, IAM and all sorts of amazing new...
Playing with MS14-060 and MS14-058 [CVE-2014-4113 CVE-2014-4114] : Attacks and Defenses
Recently two 0-day exploits were revealed. The first one was given the name Sandworm, however, the name convention was mistakenly including the "worm" term as we will see. The second one CVE-2014-4113 is a privilege escalation local exploit for Windows. Sandworm as said includes the word "worm" most likely for making the situation more dramatic. A worm is a self-propagating piece of code that...
GPU Password Cracking Hype
Ditch the CPU for password cracking even if you have an overclocked Extreme Intel Core i7, they just aren't made for password cracking since they only contain a small number of cores. Instead set your sights on a high powered graphics cards with with the primary aim of finding cards with a high number of cores, for instance the GeForce GTX TITAN Z features a whopping 5760 cores. Imagine the...
Disclaimer
The information provided on this website is to be used for educational purposes only. The author is in no way responsible for any misuse of the information provided. Any actions and or activities related to the material contained within this website is solely your responsibility.