Hello there, in this post I will describe how I solved the cloudfs challenge of Ghost In The Shellcode 2015. This challenge was under the Forensics category and was awarded 200 points (middle ground!). It wasn’t so hard, and someone could argue that shouldn’t award the same points with “the alpha molecular” or the similars from the crypto category but it’s okay (it’s very common actually in every CTF to argue about points etc..). The point of that challenge was that it was using ICMP (so there isn’t any TCP Follow Stream option…) and that the file that was included was scattered across multiple packets.
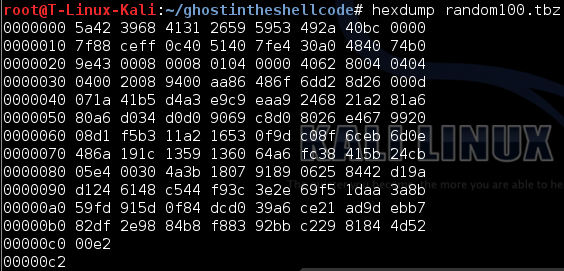
So the file of the challenge was an .xz file meaning that we had to decompress it first.
xz file awaits
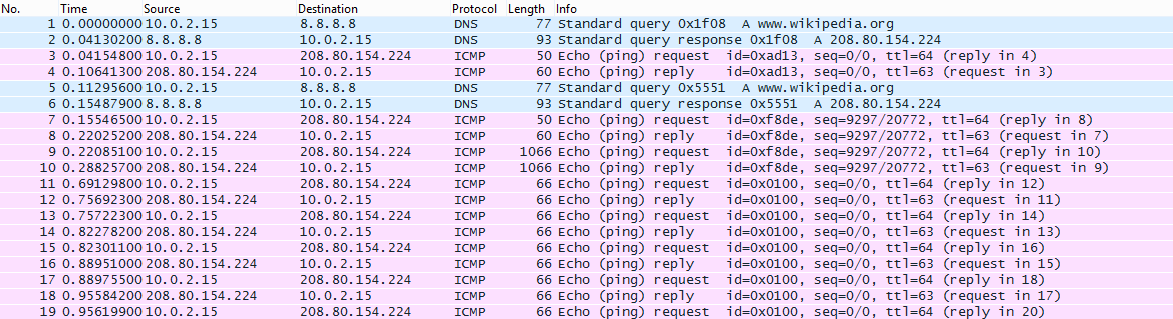
We open the pcap file with wireshark and we see all these ICMP ping requests/replies.
By doing tshark -r pcapfile -T fields -e data -w outputfilee ; strings outputfilee we can dump all the data from the pcap and search for ASCII characters. There is a bunch of delicious apples and ripe yellow bananas there (at some point I thought that the key is something related to that!).
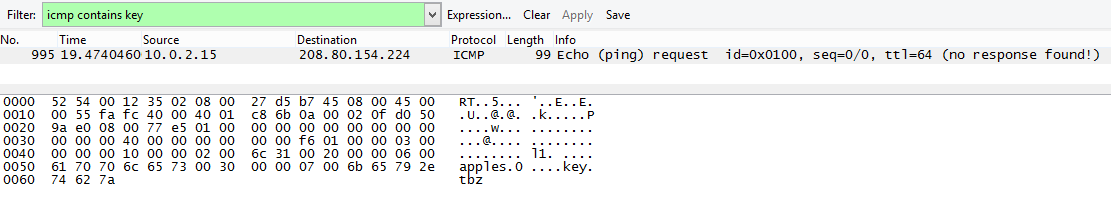
Since I was searching for the key I did the following filter initially icmp contains key and manage to find a packet that was giving away the existence of a key.tbz file. So I know that there is a tbz file somewhere around…
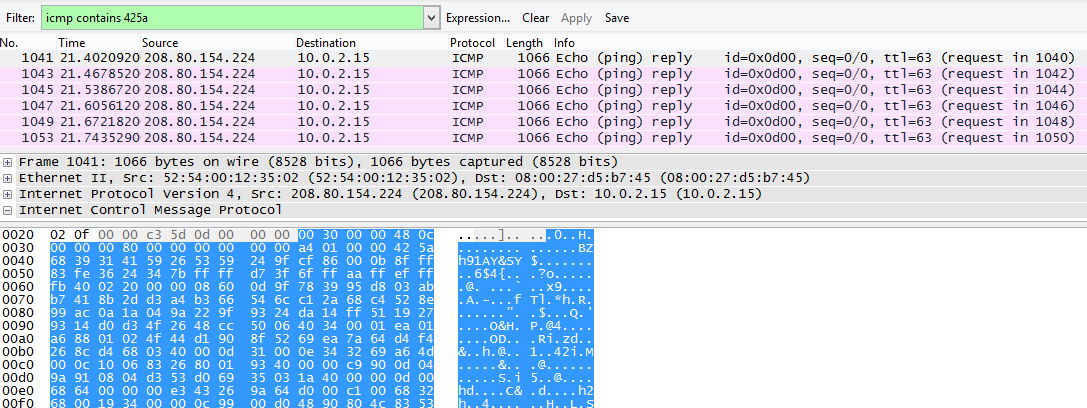
I created a file and make it .tbz to see the header and right after I updated my wireshark filter to icmp contains 425a
The data section of the first [No. 1041] packet ended with the bytes “da 61”. I saw that the replies where basically having the same data so I filtered em out.
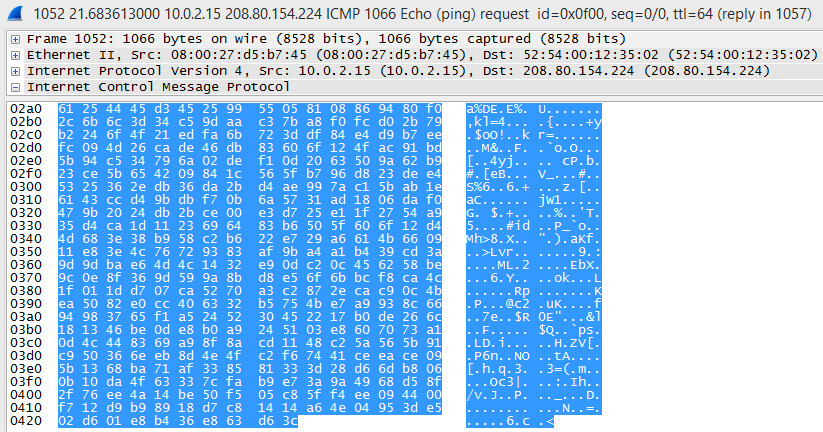
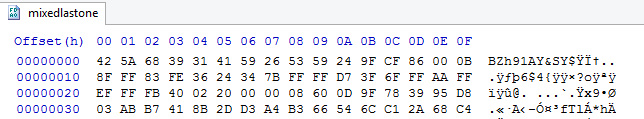
Then the 2nd piece of the tbz file is in packet [No. 1051] ending with bytes “30 98”. The 3rd piece was in the next packet [No. 1052]. Then there is a series of packet exchanges with these 3 pieces and in packet [No. 1075] it is the last part of the .tbz file which ends with bytes “f0 c0”. I exported these 4 data sections of these packets and then I used the HxD editor for copy/paste the bytes (I had also to remove some bytes from the first packet’s data section)
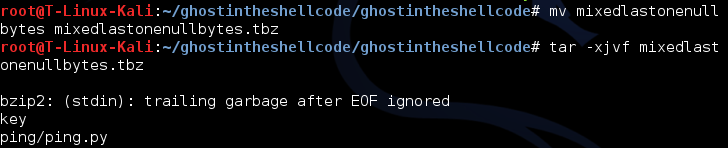
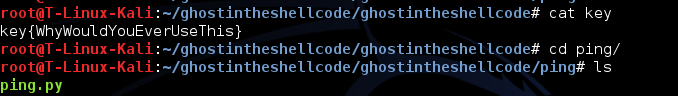
I renamed the file to be able to extract it and then that was it. The ping.py was also included in that tbz file!