My Perspective on MFA Security
In an era of relentless cyber threats, multi-factor authentication (MFA) has become a cornerstone of modern security practices, adding an extra layer of protection beyond traditional passwords. It’s a widely used defence that strengthens account security and helps prevent unauthorised access. But while MFA is a crucial security measure, it’s not a silver bullet. Cybercriminals are constantly adapting, finding new ways to bypass or manipulate different authentication methods. Whether it’s phishing, machine-in-the-middle attacks, MFA fatigue, or social engineering, no authentication mechanism is completely immune.
In this blog post, I’ll explore the various methods used to protect user credentials and rank the most common MFA mechanisms based on how vulnerable they are to the types of attacks we’re seeing in today’s threat landscape. Multi-Factor Authentication (MFA) is all about making it harder for attackers to break in by requiring users to verify their identity using multiple factors before accessing an account or system. These factors generally fall into three categories:
- Something you know (e.g., a password or PIN)
- Something you have (e.g., a smartphone, security key, or token)
- Something you are (e.g., a fingerprint or facial recognition)
MFA strengthens security by adding layers beyond just passwords, reducing the risk of account takeovers. But not all MFA methods are created equal! Some are far more resistant to phishing, social engineering, and technical exploits than others.
At the same time, password-less authentication is becoming more popular as a way to move beyond passwords altogether. Instead of relying on something you have to remember, it uses factors like biometrics (i.e. fingerprints, facial features, etc.) or device-based authentication, making logins both more secure and more user-friendly. While this approach has clear advantages, it also comes with challenges in adoption and implementation.
Drawing from my experience, I’ll be ranking these methods by how secure they are, how easy they are to use, and how challenging it can be to implement them.

How I Evaluated These MFA Methods
Cost is an essential factor when evaluating MFA solutions. Some methods, such as SMS-based authentication, may seem inexpensive but can lead to high recurring costs. Others, like hardware security keys, require upfront investments and logistical considerations. Throughout this ranking, I factor in the costs associated with implementation, user adoption, and long-term maintenance.
To fairly compare different MFA methods, I evaluated them based on three main factors:
- Security: How resistant is the method to common attacks such as phishing, SIM swapping, MFA fatigue, and adversary-in-the-middle (AiTM) attacks?
- Usability: How easy is it for end users to adopt and use the method effectively? This considers user experience, commonality among MFA adopters, and interaction simplicity.
- Implementation: How complex is it for organisations to implement this method? This includes factors such as deployment effort, compatibility with existing systems, and cost considerations.
Each factor is ranked on a scale from 1 to 10, with higher scores indicating stronger security, better usability, or easier implementation. Some methods may offer excellent security but can be more difficult to implement or less user-friendly.
Common MFA Attack Methods
Despite MFA’s advantages, threat actors continue to develop techniques to bypass it. Some of the most notable attack methods include:
- Phishing Attackers trick users into entering their credentials and MFA codes into malicious websites (e.g., AiTM attacks using tools like Modlishka, Evilginx, and Muraena). [1]
- SIM Swapping Criminals exploit flaws in telecommunications protocols to hijack SMS-based MFA codes. The FBI has reported significant increases in SIM swapping attacks, with millions in losses.[2]
- MFA Fatigue: Attackers flood users with push notifications, as seen in the 2022 Uber breach. [3]
- SS7 Exploits: Flaws in the telephone system protocols allow attackers to intercept OTPs and hijack calls.[4]
Let’s now dive in as I rank MFA methods based on my experience and observations in the field.
SMS and Voice-Based MFA (Least Secure, Highly Vulnerable to SIM Swapping & SS7 Exploits)
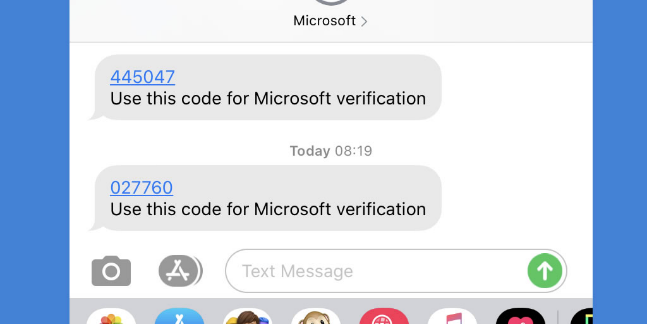 This is probably the most well-known and widely used MFA method. When you log into a website or service, it sends a one-time passcode (OTP) to your phone via SMS or a voice call. The idea is that only the real account owner should have access to their registered phone number, making it a second layer of authentication. However, as I’ve seen in many real-world attacks, this method has significant weaknesses due to SIM swapping and telecom vulnerabilities.
This is probably the most well-known and widely used MFA method. When you log into a website or service, it sends a one-time passcode (OTP) to your phone via SMS or a voice call. The idea is that only the real account owner should have access to their registered phone number, making it a second layer of authentication. However, as I’ve seen in many real-world attacks, this method has significant weaknesses due to SIM swapping and telecom vulnerabilities.
- Cost Considerations: Recurring costs for sending SMS messages can add up, especially for large organisations. Additionally, mobile carrier dependencies can introduce extra fees or service reliability concerns.
- Security: 3/10 (Highly vulnerable to phishing, SIM swapping, and SS7 attacks)
- Usability: 8/10 (Simple for users, widely adopted)
- Implementation: 9/10 (Easy to deploy but incurs SMS costs)
Case studies have shown attackers using SIM swapping and SS7 exploits to intercept OTPs. [2],[4]
Given these risks, SMS MFA is the least secure option and shouldn’t be used for organisations, or individuals of interest who may be targeted by threat actors, or to access critical systems.
App-Based OTP (Better but Still Phishable)
 Instead of relying on SMS, app-based OTPs generate codes through applications like the Google or Microsoft Authenticator Apps, Authy, Okta, or other applications available to users who want to take advantage of this added layer of security. When you attempt to log in, the app can be accessed to retrieve a time-sensitive code (or One-Time Password) from your device to finalise the authentication process. This removes dependency on mobile networks, which is a big advantage, but as observed in the wild, through phishing attacks users can still be tricked into entering such codes into fake login pages.
Instead of relying on SMS, app-based OTPs generate codes through applications like the Google or Microsoft Authenticator Apps, Authy, Okta, or other applications available to users who want to take advantage of this added layer of security. When you attempt to log in, the app can be accessed to retrieve a time-sensitive code (or One-Time Password) from your device to finalise the authentication process. This removes dependency on mobile networks, which is a big advantage, but as observed in the wild, through phishing attacks users can still be tricked into entering such codes into fake login pages.
- Cost Considerations: Generally free for users but requires administrative overhead to ensure proper deployment. Organisations may need to invest in user training to prevent phishing risks.
- Security: 6/10 (Resistant to SIM swapping but vulnerable to phishing and AiTM attacks)
- Usability: 8/10 (Requires manual entry, increasing user friction)
- Implementation: 8/10 (Easier than hardware keys but still needs user training)
Attackers have successfully used AiTM techniques to bypass OTPs [5].
Security researchers have documented real-world cases where Evilginx and similar frameworks were used to steal cookies from authenticated sessions, bypassing MFA without needing to steal OTPs.
Push Notifications (Susceptible to MFA Fatigue Attacks)
 Push notifications work differently from OTPs. Instead of manually entering a code, you receive a notification on your phone asking if you’re trying to log in. You simply tap ‘Approve’ or ‘Deny.’ This makes authentication experience much smoother for users. However, attackers have learned to exploit this through MFA fatigue attacks, where users are bombarded with requests until they approve one by mistake.
Push notifications work differently from OTPs. Instead of manually entering a code, you receive a notification on your phone asking if you’re trying to log in. You simply tap ‘Approve’ or ‘Deny.’ This makes authentication experience much smoother for users. However, attackers have learned to exploit this through MFA fatigue attacks, where users are bombarded with requests until they approve one by mistake.
- Cost Considerations: Low implementation costs but may require additional monitoring and security awareness training to prevent MFA fatigue attacks.
- Security: 7/10 (Stronger than OTPs but vulnerable to MFA fatigue attacks)
- Usability: 9/10 (Simplifies authentication)
- Implementation: 7/10 (Easy to deploy, but requires monitoring)

The 2022 Uber breach exemplified how MFA fatigue attacks can lead to compromise [6].
This attack vector is increasingly leveraged by cybercriminals. Identity providers have tried to tackle this issue by introducing number matching, where a number is displayed to the user trying to authenticate, expecting the user to enter the same number when approving the authentication request received on their phone.
Hardware Security Keys (Strong, Phishing-Resistant)
 Hardware security keys, such as YubiKey and Google Titan, provide one of the strongest forms of MFA. These small physical devices must be plugged into or tapped against a device to approve authentication. They use cryptographic signatures that cannot be phished. I personally find them to be a fantastic option for security-conscious individuals and organisations, but they do require carrying an extra device and managing lost keys.
Hardware security keys, such as YubiKey and Google Titan, provide one of the strongest forms of MFA. These small physical devices must be plugged into or tapped against a device to approve authentication. They use cryptographic signatures that cannot be phished. I personally find them to be a fantastic option for security-conscious individuals and organisations, but they do require carrying an extra device and managing lost keys.
- Cost Considerations: High upfront cost for purchasing hardware tokens (e.g., YubiKeys), along with logistical challenges related to distribution and lost key replacements.
- Security: 9/10 (Resistant to phishing and AiTM attacks)
- Usability: 7/10 (Requires carrying a physical device, potential lockouts)
- Implementation: 6/10 (Higher cost and logistical challenges)
Hardware keys such as are among the most secure MFA solutions [7].
However, distribution and lost key management remain challenges.
Passkeys & FIDO2 (Best Option, Eliminates Passwords and Phishing Risks)
 Passkeys and FIDO2/WebAuthn take authentication a step further by eliminating passwords altogether. These methods use cryptographic keys that are stored securely on your device and verified using biometrics or a PIN. In my opinion, this is where authentication is headed—no passwords to steal and no OTPs to phish. However, adoption is still growing, and not every service supports it yet.
Passkeys and FIDO2/WebAuthn take authentication a step further by eliminating passwords altogether. These methods use cryptographic keys that are stored securely on your device and verified using biometrics or a PIN. In my opinion, this is where authentication is headed—no passwords to steal and no OTPs to phish. However, adoption is still growing, and not every service supports it yet.
- Cost Considerations: Requires infrastructure updates but eliminates the need for passwords, reducing long-term costs associated with password resets and credential management.
- Security: 10/10 (Eliminates phishing risks by design)
- Usability: 9/10 (Simplifies authentication, biometric support)
- Implementation: 8/10 (Requires infrastructure changes, but worth the investment)
Passkeys and FIDO2 authentication represent the future [8].
Given their phishing-resistant nature, I ranked them highest in security, though adoption requires investment.
Best Practices for Implementing Secure MFA
A number of best practices and recommendations have been outlined by frameworks such as CIS benchmarks, cloud providers, and SaaS (Software-as-a-Service) vendors.
While the most appropriate MFA mechanism depends on an organisation’s specific needs, at a high level, I can offer the following advice:
- Monitor authentication logs: Identify risky sign-ins and detect anomalous authentication attempts.
- Enforce phishing-resistant MFA: Prioritise Pass-keys & FIDO2 security keys or, at least, biometric-based authentication.
- Implement Adaptive Authentication: Evaluate risk factors such as user behaviour, device compliance, and location checks.
- Deploy Conditional Access Policies (CAPs) for Microsoft Environments: Particularly useful for Microsoft-centric organisations, but not always applicable to all setups.
To conclude, I have explored various MFA methods and how they stack up against real-world attacks. There is no perfect solution, but the shift towards password-less authentication, adaptive security controls, and phishing-resistant methods is clear. Security is an ongoing challenge, and no control is ever enough to completely eliminate risk. Organisations must continuously evolve their security strategies and follow a proactive approach considering the latest threat intelligence and attack trends.
Ultimately, the best MFA method is the one that aligns with an organisation’s security posture, usability needs, and implementation capabilities. As cyber threats grow more sophisticated, adopting robust MFA solutions is not just a best practice—it’s a necessity.
References
- [1] Verizon Data Breach Investigations Report, 2023 – https://www.verizon.com/business/en-gb/resources/reports/dbir/2023/summary-of-findings/#:~:text=83%25%20of%20breaches%20involved%20External,phishing%20and%20exploitation%20of%20vulnerabilities.
- ]2] FBI Internet Crime Report, 2022 – https://www.ic3.gov/PSA/2022/PSA220208
- [3] Microsoft Tech Community, 2022 – https://techcommunity.microsoft.com/blog/microsoft-entra-blog/defend-your-users-from-mfa-fatigue-attacks/2365677
- [4] FBI and CISA Warn Against SMS OTP Authentication Amidst Escalating Cyber Security Risks, 2025 – https://www.keypasco.com/en/2025/02/04/fbi-and-cisa-warn-against-sms-otp-authentication-amidst-escalating-cybersecurity-risks/
- [5] Phishing 2.0 – how phishing toolkits are evolving with AitM, 2024 – https://pushsecurity.com/blog/phishing-2-0-how-phishing-toolkits-are-evolving-with-aitm/
- [6] What Caused the Uber Data Breach in 2022? –https://www.upguard.com/blog/what-caused-the-uber-data-breach#:~:text=the%20Uber%20app.-,What%20Data%20Did%20the%20Hacker%20Access?,with%20cybersecurity%20researcher%20Corben%20Leo
- [7] What Is a Hardware Security Key and How Does It Work?, 2023 – https://www.keepersecurity.com/blog/2023/05/09/what-is-a-hardware-security-key-and-how-does-it-work/
- [8] FIDO Alliance Whitepaper, 2023 – https://fidoalliance.org/passkeys/
