Bypassing Antivirus with Golang – Gopher it!
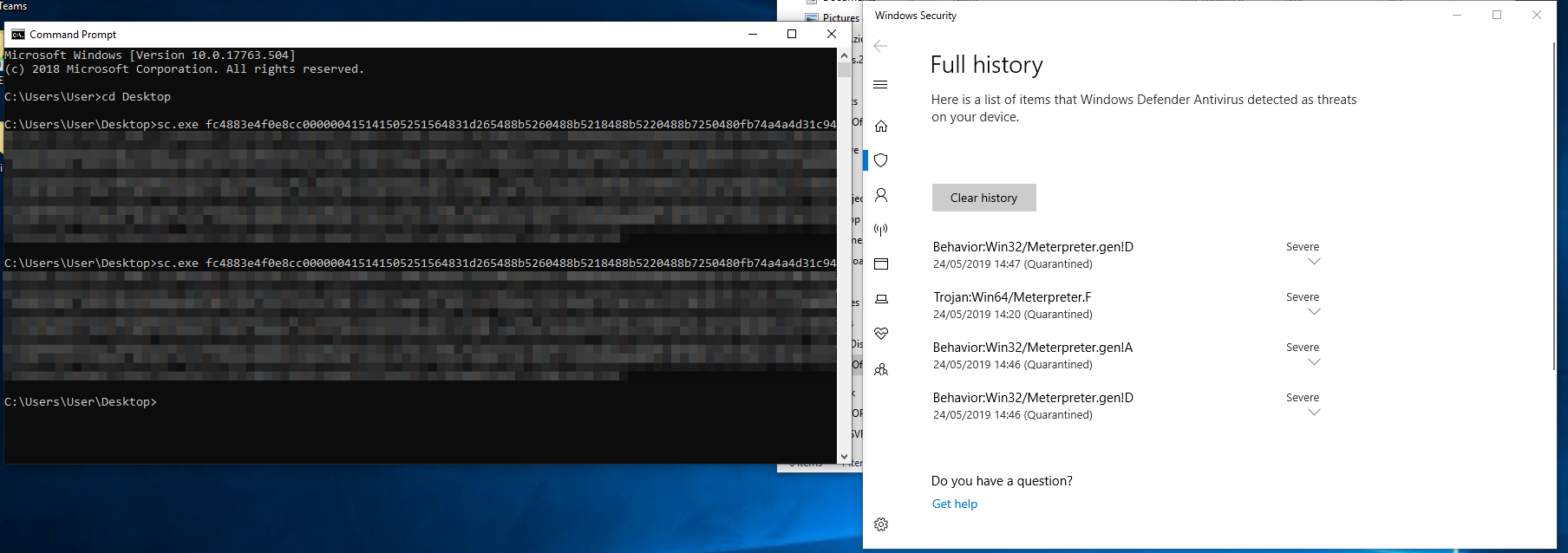
In this blog post, we’re going to detail a cool little trick we came across on how to bypass most antivirus products to get a Metepreter reverse shell on a target host. This all started when we cam...

In this blog post, we’re going to detail a cool little trick we came across on how to bypass most antivirus products to get a Metepreter reverse shell on a target host. This all started when we cam...

In this blog post I am going to tackle the topic of detecting common attacks using Active Directory logs. It is important to understand the power of data in InfoSec world. Too much data means you’l...

“Indicator of compromise (IOC) in computer forensics is an artifact observed on a network or in an operating system that with high confidence indicates a computer intrusion. Typical IOCs are virus ...
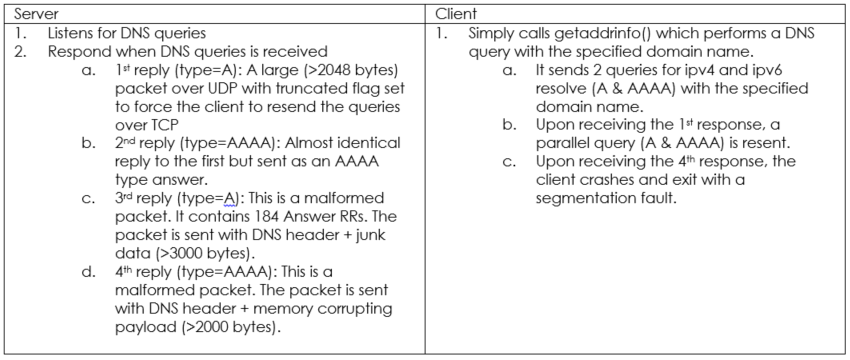
Hello w0rld! JUMPSEC researchers have spent some time on the glibc DNS vulnerability indexed as CVE 2015-7547 (It hasn’t got a cool name like GHOST unfortunately…). It appears to be a highly critic...

Hello w0rld. On this post we would like to let you know our areas of research and the research projects that we are working on currently. For 2016 we are planning to develop tools that will be used...

Hello w0rld. In this post I will show how it is possible to (mis)use ICMP protocol for file transfers with scapy. “In computer security, a covert channel is a type of computer security attack that...
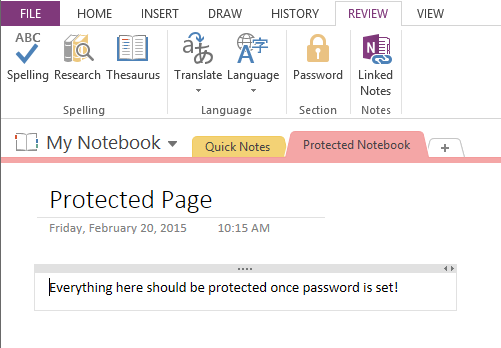
Bug Summary A security bug in the Microsoft Onenote allows images placed in user-created password-protected sections to be cached persistently in the user profile temporary directory folder: C:\U...
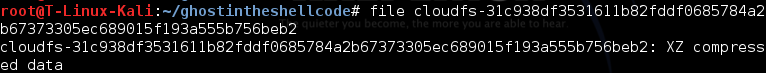
Hello there, in this post I will describe how I solved the cloudfs challenge of Ghost In The Shellcode 2015. This challenge was under the Forensics category and was awarded 200 points (middle groun...

Computer systems and software have been continually evolving year upon year. Faster processing and data transfer coupled with more accessible storage have made crunching vast amounts of data possi...
![Playing with MS14-060 and MS14-058 [CVE-2014-4113 CVE-2014-4114] : Attacks and Defenses](/assets/img/posts/playing-ms14-060-ms14-058-cve-2014-4113-cve-2014-4114-attacks-defenses/sandworm-options.png)
Recently two 0-day exploits were revealed. The first one was given the name Sandworm, however, the name convention was mistakenly including the “worm” term as we will see. The second one CVE-2014-4...