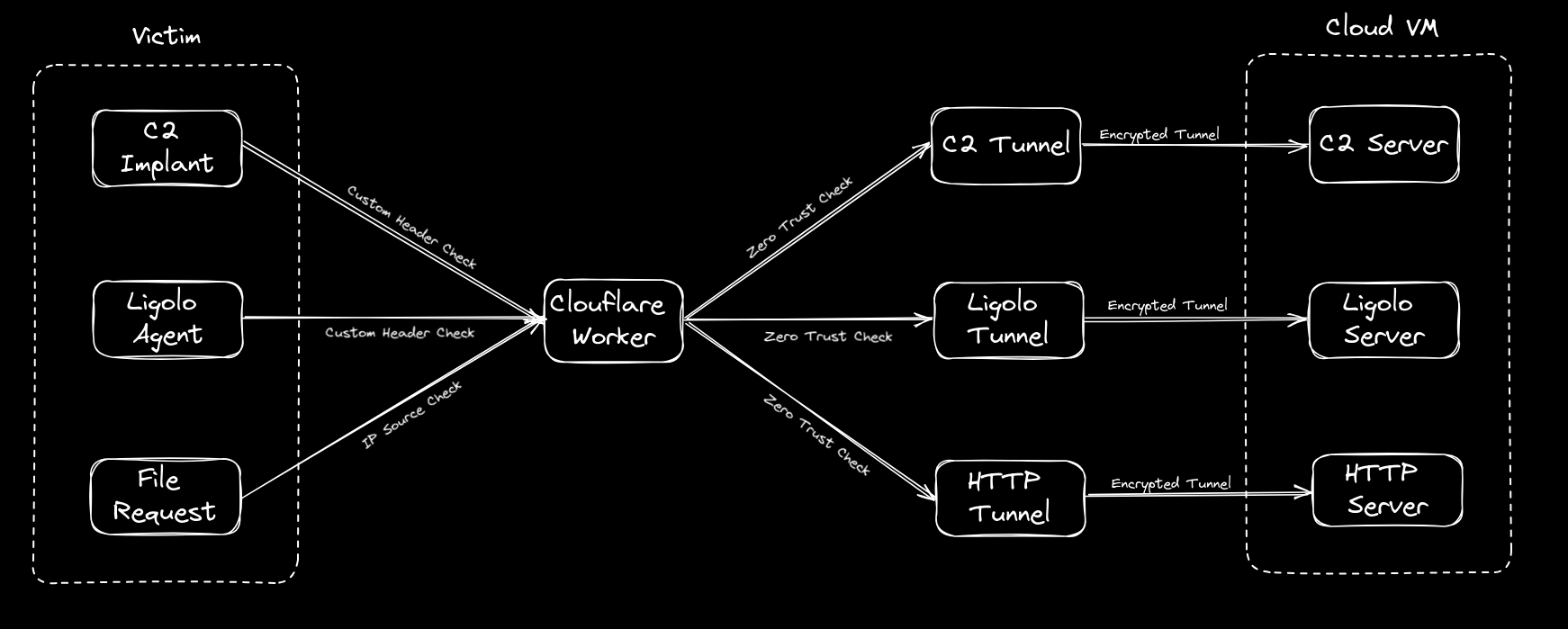
Putting the C2 in C2loudflare
tl;dr How to bring up an entire C2 infrastructure with all your tooling and their corresponding redirectors within 5 minutes with the help of Azure Snapshots, Cloudflare and Tmux Resurrect. Every...

tl;dr How to bring up an entire C2 infrastructure with all your tooling and their corresponding redirectors within 5 minutes with the help of Azure Snapshots, Cloudflare and Tmux Resurrect. Every...
In this labs post, I will introduce you to modern security controls that are currently used (but not always correctly) by the vast majority of enterprises, and hopefully by the end of this write-up...

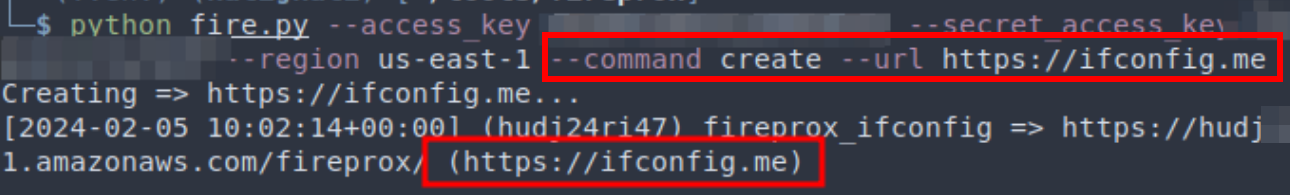
In Part 1 of the series we looked at how an AWS Lambda-powered feature was exploited in a web app penetration test initially leading to RCE and further on with out-of-band data exfiltration via DNS...

This is a war story of an AWS web application test where remote code execution was first obtained on the client’s application. Then I needed to write my own DNS tunnelling ‘protocol’ to get the dat...

*** TL;DR*** This blog post introduces Web Assembly (WASM) as a powerful alternative to traditional web technologies, highlighting its appeal to cybersecurity professionals for evading security m...

Hello World! So, I’ve been tinkering with network stuff lately, trying to set up some infrastructure.Turns out that in the process, I made a rookie mistake and left a few ports open to the internet...

Introduction In the ever-evolving realm of cloud services, organisations are ditching the headaches of physical infrastructure management and diving headfirst into the possibilities of cloud platf...
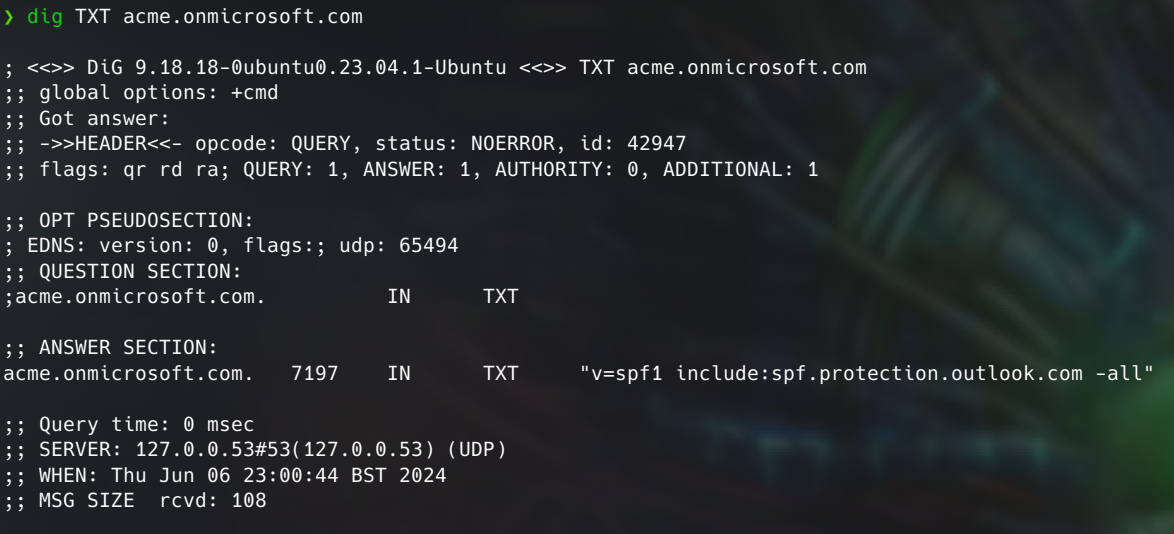
In 2023 through 2024, JUMPSEC’s red team gained access to Microsft 365 (M365) environments of sophisticated clients during adversarial engagements with an approach that breathes life into the decad...

Software: IBM SAN Volume Controller, IBM Storwize, IBM FlashSystem and IBM Storage Virtualize products Affected versions: 8.3 Vendor page: https://www.ibm.com/support/pages/node/7064976 CVE Refe...

Introduction Cloud adoption is exploding, and rightfully so. Businesses are seeing the value of improved agility and efficiency when leveraging public cloud, resulting in 60% of all corporate data...